2025 第二届"Parloo 杯"CTF 应急响应挑战赛 RE wp
PositionalXOR
根据题目描述可知加密算法就是xor
附件里就一个bin文件,010editor打开,数据提出来直接写脚本解密
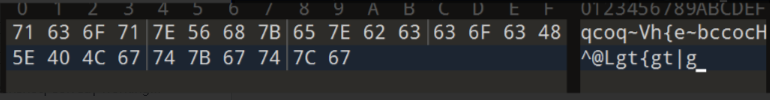
1 | enc = "qcoq~Vh{e~bccocH^@Lgt{gt|g" |
PaluArray
UPX壳,并且好像有的标志位被删了,直接x64dbg手动脱壳,然后ida分析,根据提示字符串定位到程序的主要逻辑
1 | // Hidden C++ exception states: #wind=2 |
这里就是处理输入密文的函数,sub_7FF61DC51994函数对字符串的每个字符进行查找,在一个确定的table中
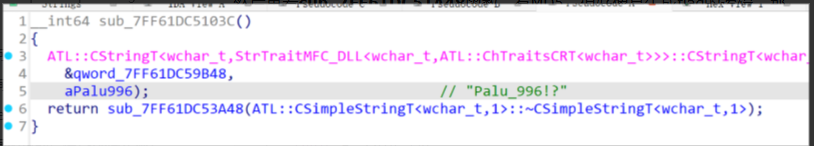
然后再看sub_7FF61DC51A48函数,有MD5,但好像是生成flag的逻辑,那么应该就是将上面解密出来的字符串输入进去,就会输出flag
解密脚本
1 | table = "Palu_996!?" |
得到:aa_9a_a?a?!aP
然后运行程序输入
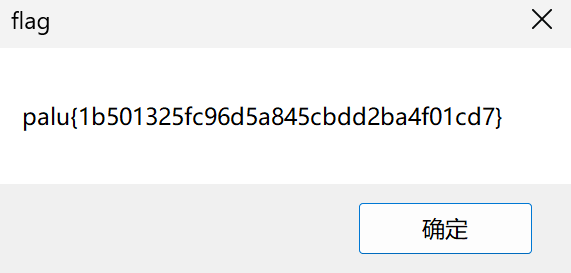
PaluGOGOGO
go语言,ida打开分析
主要加密逻辑
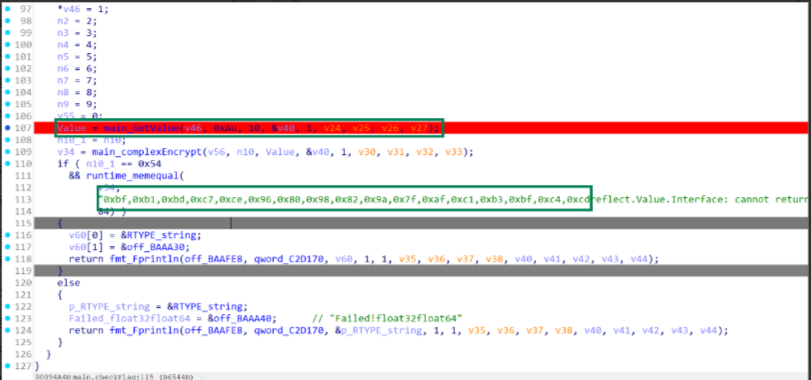
红色部分是密文,绿色部分获取的value会传入到main_complexEncrypt参与flag的加密
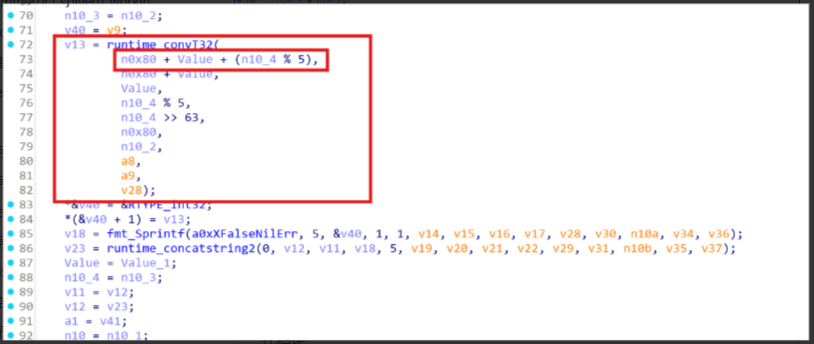
加密逻辑如图,value就是在外面传进来的值,n10_4是index
解密脚本
1 | enc = [0xbf,0xb1,0xbd,0xc7,0xce,0x96,0x80,0x98,0x82,0x9a,0x7f,0xaf,0xc1,0xb3,0xbf,0xc4,0xcd] |
PaluFlat
ida打开附件 发现密文
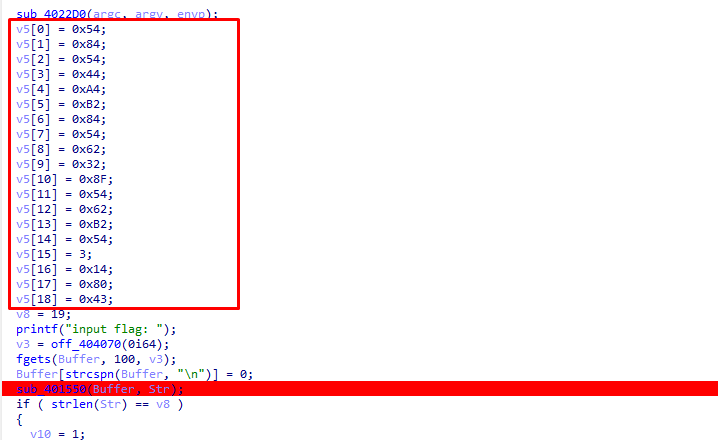
加密算法是sub_401550 跟进一下
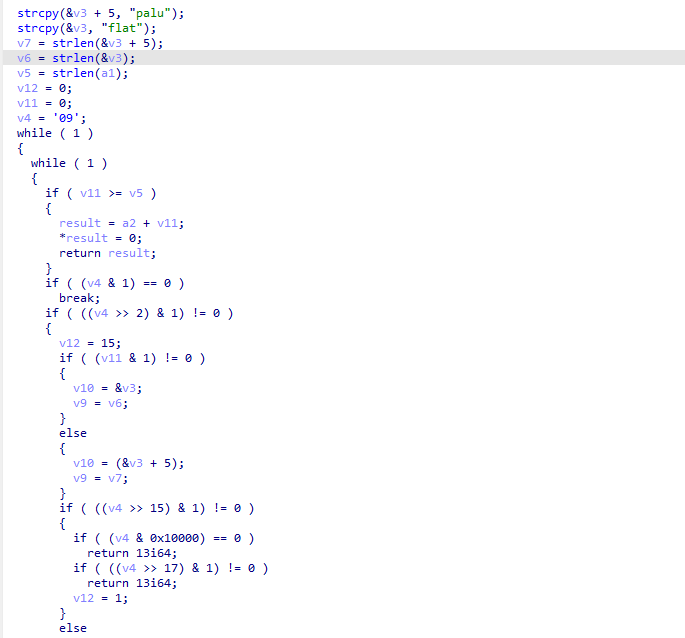
主要逻辑就是 根据奇数偶数选择对应的密钥 输入跟密钥循环异或 半字节交换 减0x55 取反
直接对着写逆向脚本即可
1 | key1 = b"flat" |
Asymmetric
ida打开附件 发现65537 第一时间想到RSA
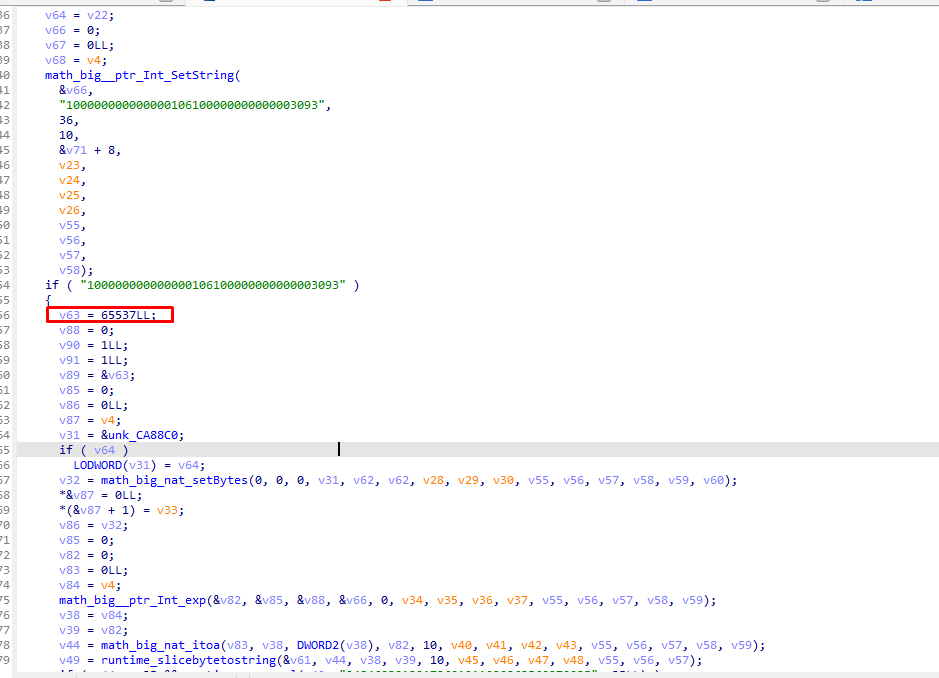
密文在下边
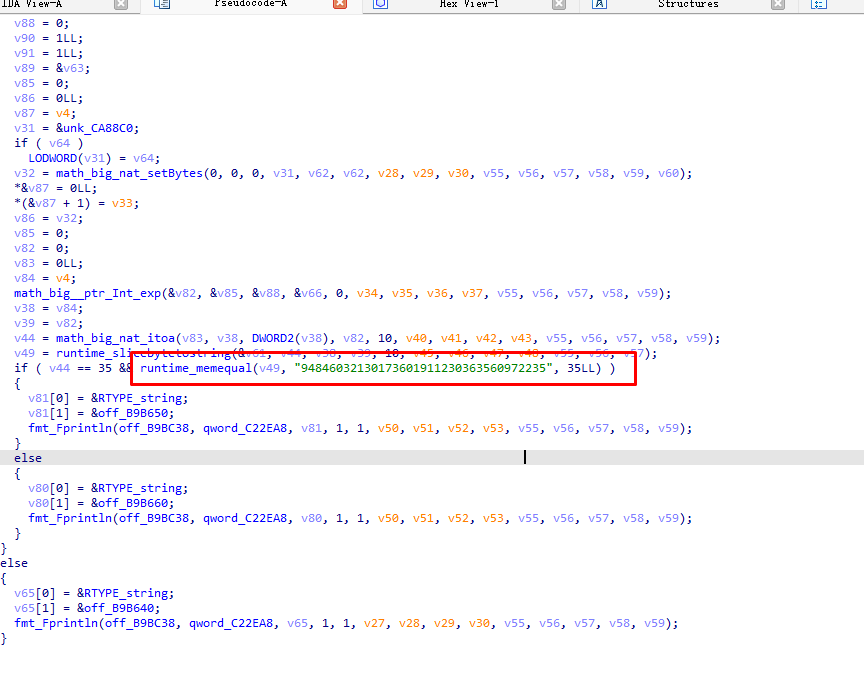
yafu分解一下n
直接写脚本解rsa
1 | import libnum |
CatchPalu
ida打开附件 常规花 nop掉 进入main函数 有个hook函数 跟进
密文密钥如下
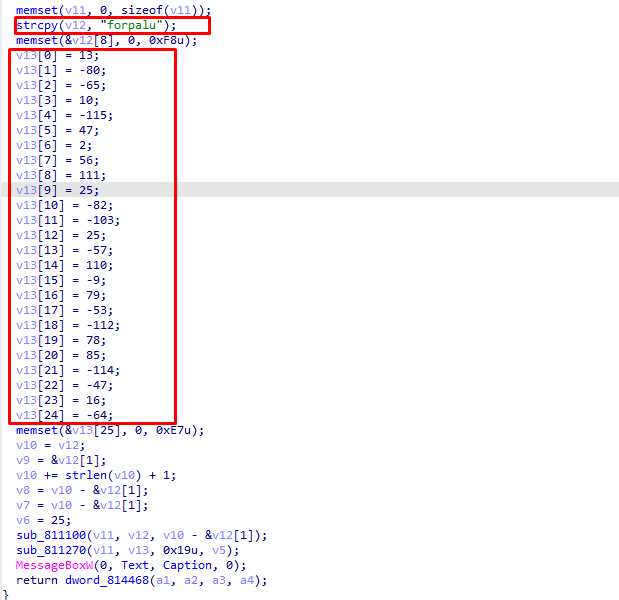
跟进下面的函数 发现是个魔改的RC4
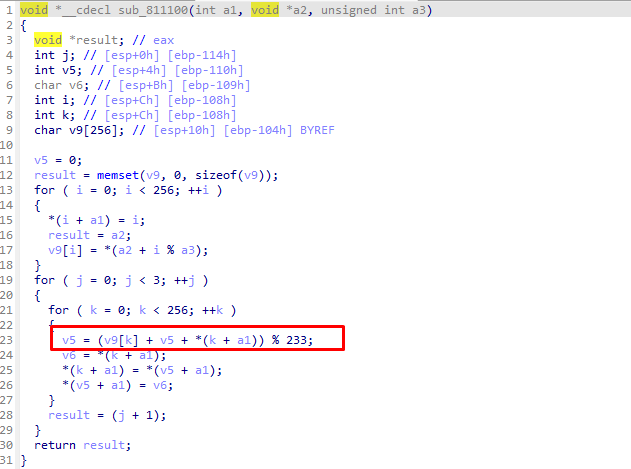
写脚本解密即可
1 | def KSA(key): |
帕鲁迷宫
无语题 python的exe 3.11 解包反编译发现往下走才会给出完整地图 还有出口 直接手动走一下 得到

那么地图如下
1 | ################################ |
搓个bfs跑一下最短路径
1 | from collections import deque |
跑出来不对 猜测有多解 经过手扣发现有的地方路径不唯一 具体如下
1 | ssssddssddwwddwwddddddddssssssssddssaaaaaaaaaawwddddwwddwwaaaassaaaaaaaassddssssa(as,sa)(sd,ds)dssssddssddssaassddssaaaaa(as,sa)(wd,dw)dddddddwwddssddwwwwddddddwwaaaaaaaaaawwwwddssddwwddssddwwwwaawwddddwwwwddddddddddwwwwaawwddwwaawwdddaaassddssaassddssssssssaawwaaaaaassssssssssssssssaaaa(as,sa)(wd,dw)ddddddddddwwddss(ds,sd) |
直接写脚本算一下符合条件的每一个的md5 提交即可(从后往前第一个就是)
1 | import re |
ssssddssddwwddwwddddddddssssssssddssaaaaaaaaaawwddddwwddwwaaaassaaaaaaaassddssssasadsdssssddssddssaassddssaaaaasadwdddddddwwddssddwwwwddddddwwaaaaaaaaaawwwwddssddwwddssddwwwwaawwddddwwwwddddddddddwwwwaawwddwwaawwdddaaassddssaassddssssssssaawwaaaaaassssssssssssssssaaaasadwddddddddddwwddssds
flag:palu{990fd7773f450f1f13bf08a367fe95ea}
Checker
安卓 主要逻辑在so 扔ida里
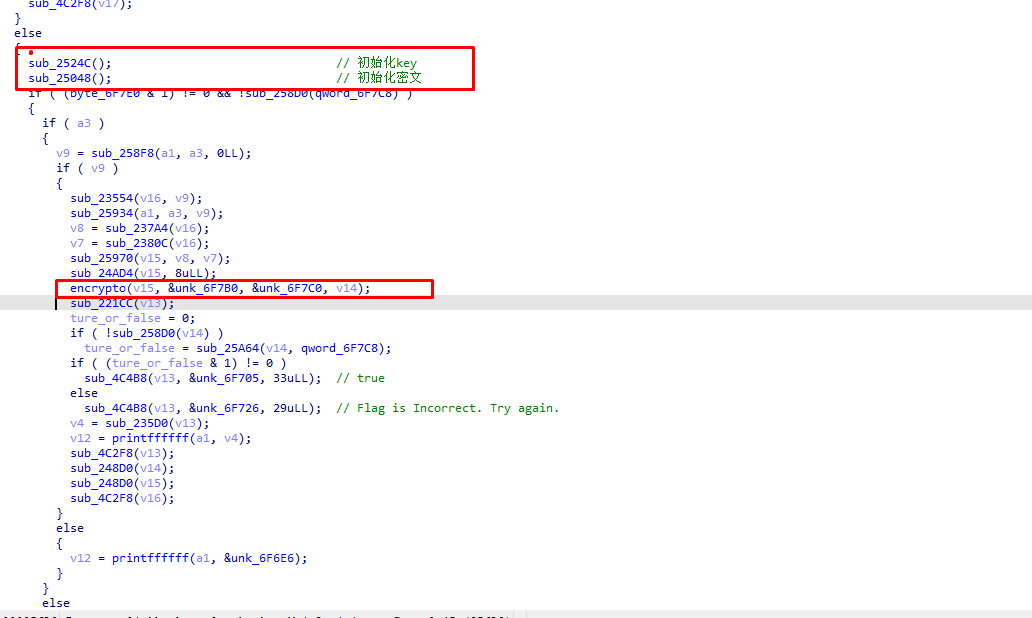
跟进一下encrypto函数
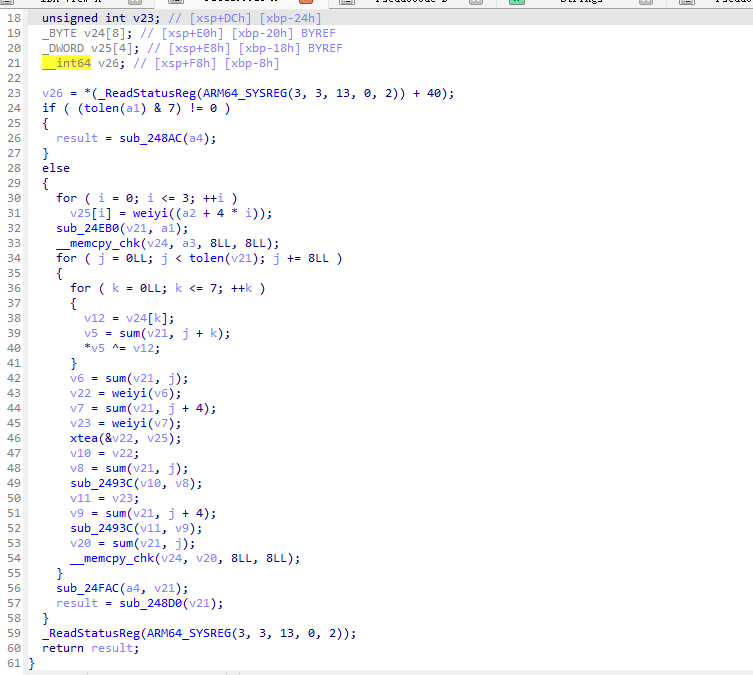
加密主要是一个cbc模式的xtea 跟进一下初始化key的函数
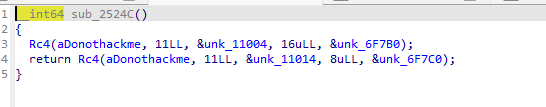
主要是对key跟iv进行一个rc4的加密 rc4的key是DoNotHackMe
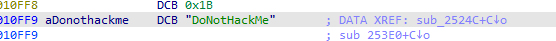
先解一下key跟iv
1 | def KSA(key): |
得到key:52756e74696d65537472696e67457874
iv:4c696e4b48405348
在解密cbc-xtea即可
1 | import struct |