2025 NSSCTF Round27 Reverse个人赛 wp
easyre
ida打开附件 根据字符串定位主要函数 有花 nop掉
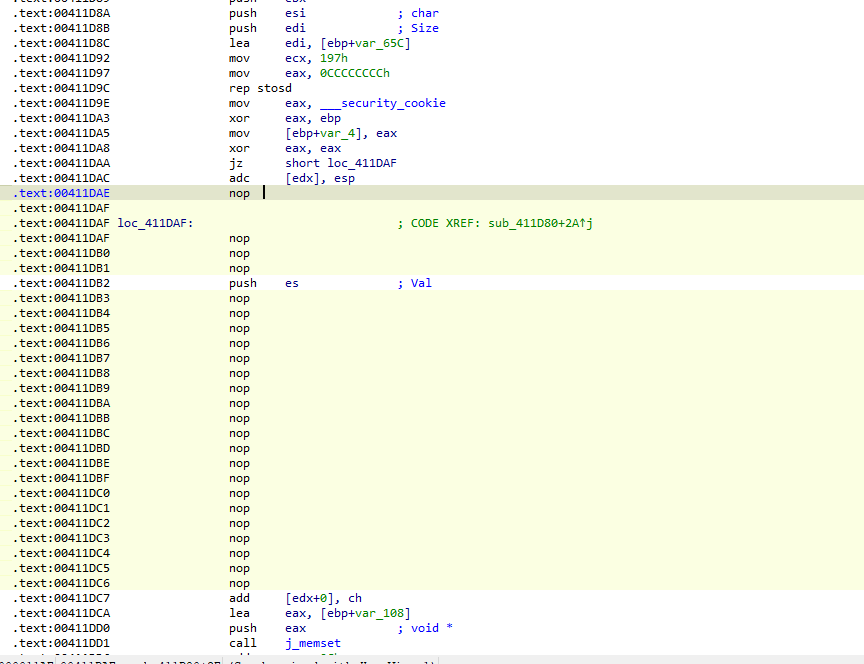
加密就是个rc4 直接找加密后的输入异或回去即可
1 | print("A" * 24) |
Ezcpp
ida打开附件 跟进加密函数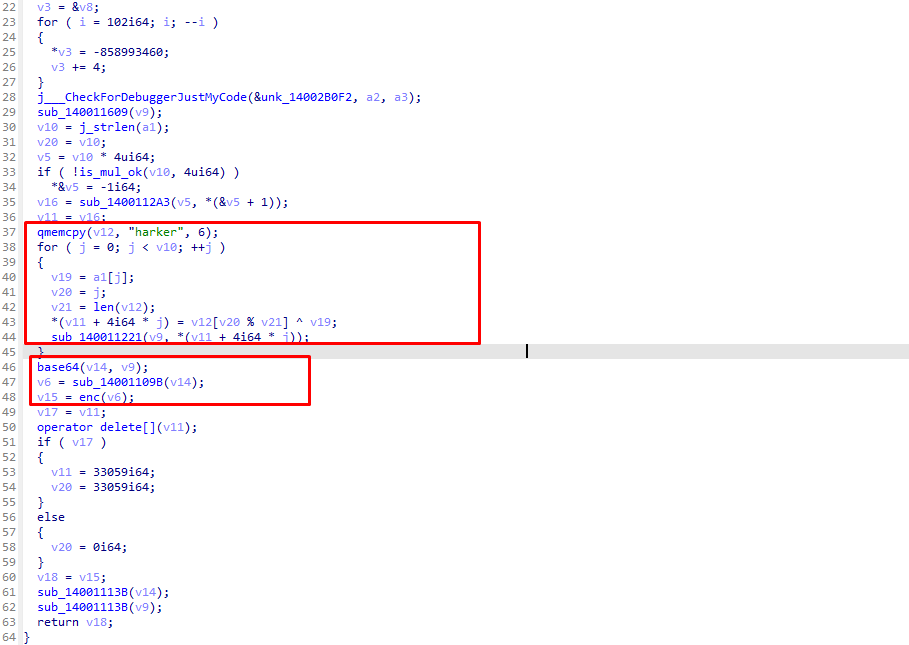
主要加密就是xor然后base64 逆着写解密即可
1 | enc = [0x0e, 0x0d, 0x13, 0x0c, 0x1e, 0x31, 0x18, 0x11, 0x2d, 0x5a, 0x50, 0x2d, 0x3e, 0x52, 0x00, 0x19, 0x1c, 0x2d, 0x5b, |
EzProcessStruct
windows的内核逆向 加密就是个xor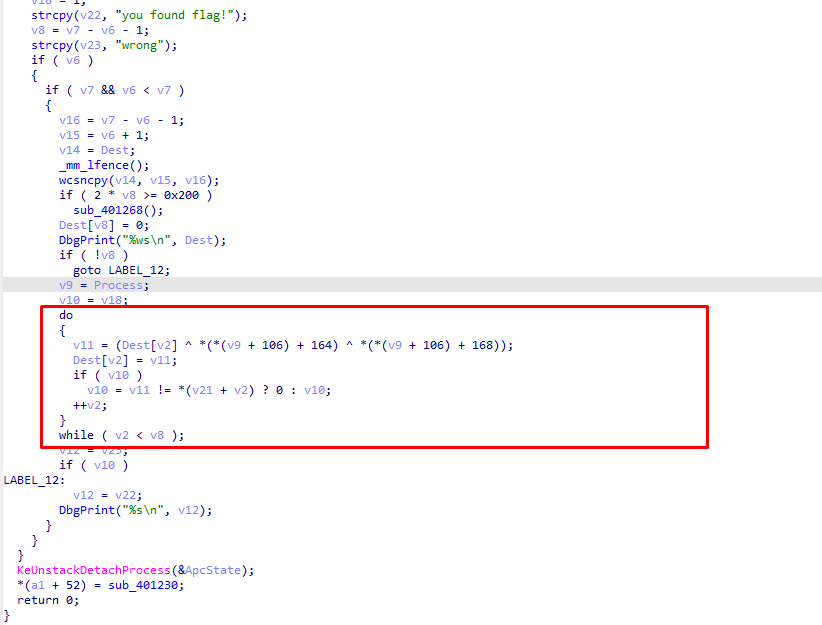
题目描述说版本号是7 直接异或回去 在解码即可
1 | import base64 |
ezminiprograme
微信小程序的逆向 先用wxappUnpacker解包 得到js文件 在app-service.js里翻到后面找到主要逻辑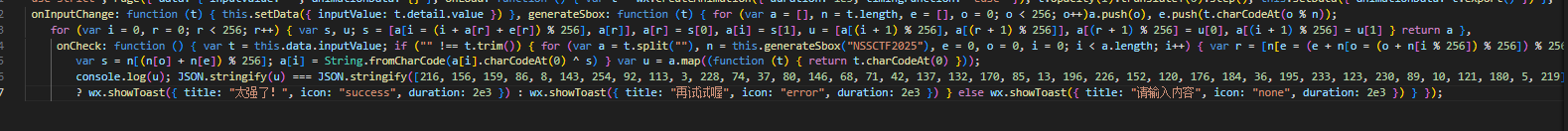
发现很多256 大概就是个RC4 正常的解不开 所以应该是魔改了 key是NSSCTF2025 密文是216, 156, 159, 86, 8, 143, 254, 92, 113, 3, 228, 74, 37, 80, 146, 68, 71, 42, 137, 132, 170, 85, 13, 196, 226, 152, 120, 176, 184, 36, 195, 233, 123, 230, 89, 10, 121, 180, 5, 219
直接扔给gpt就能写出解密
1 | def generate_sbox(key: str): |