2025 GHCTF RE wp
前言:RE的最后一题没有写 混淆和花太多 而且出题人的wp写的十分详细 我就不献丑了
ASM?Signin!
直接扔给deekseek 得到c语言代码
1 | #include <stdio.h> |
直接对照着写解密即可
1 | key = bytearray([ |
FishingKit
ida打开附件 逻辑很清晰
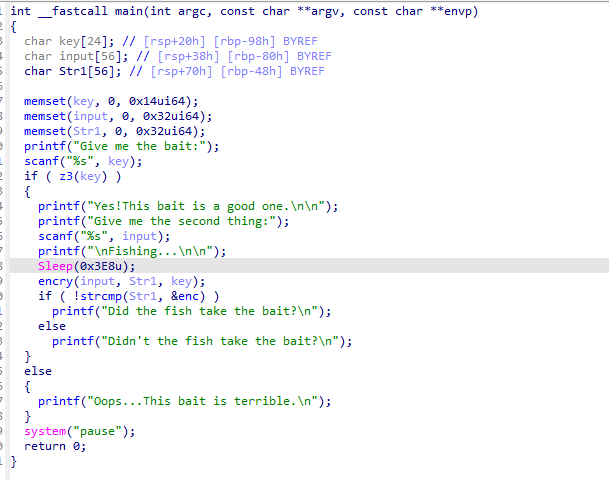
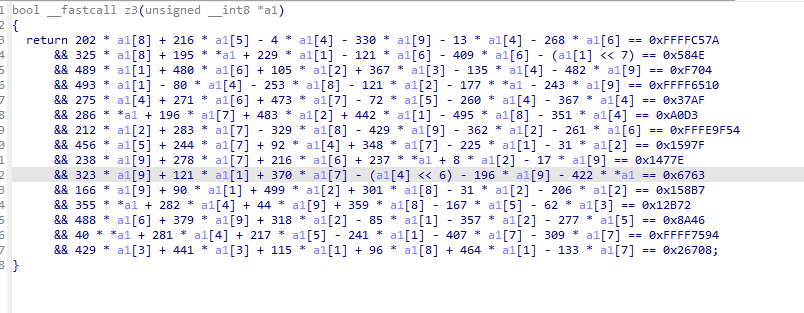
z3可以求出key
1 | from z3 import * |
随后是一个异或0x14的rc4
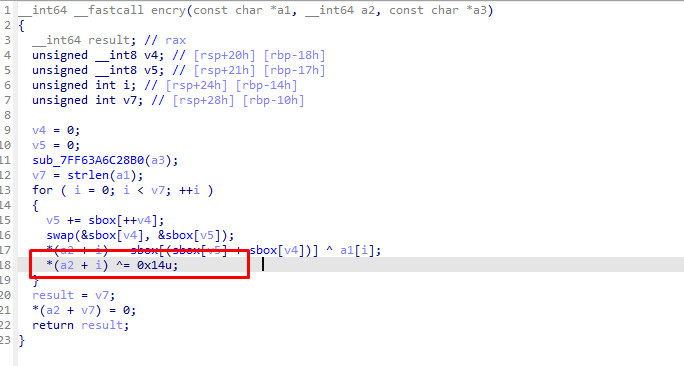
写脚本求出的是fake的flag
NSSCTF{Fake!Fake!Fake!}
随后看了看左边的函数 发现了一个函数很奇怪
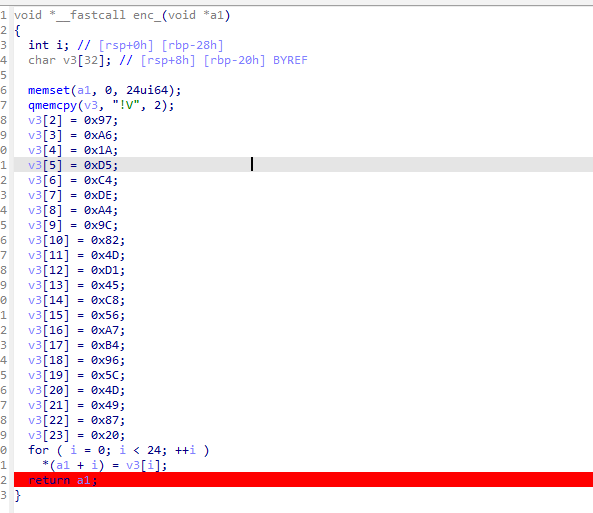
随后打个断点慢慢调试 发现在main函数调用之前进行了一个跳转
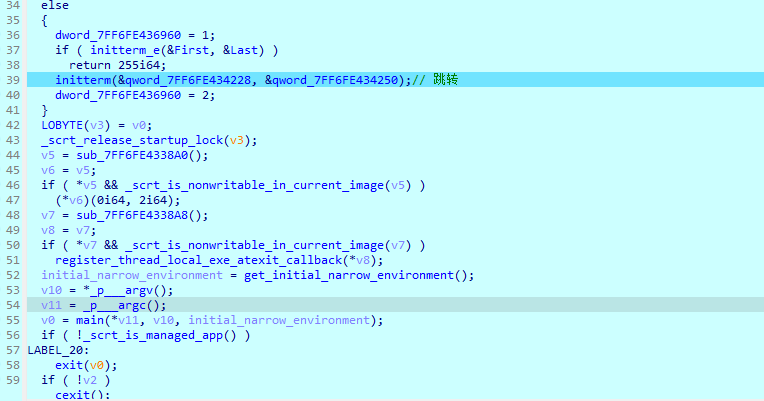
继续跟进就是之前那个奇怪的函数 交叉引用函数以及变量发现了三个tea的加密
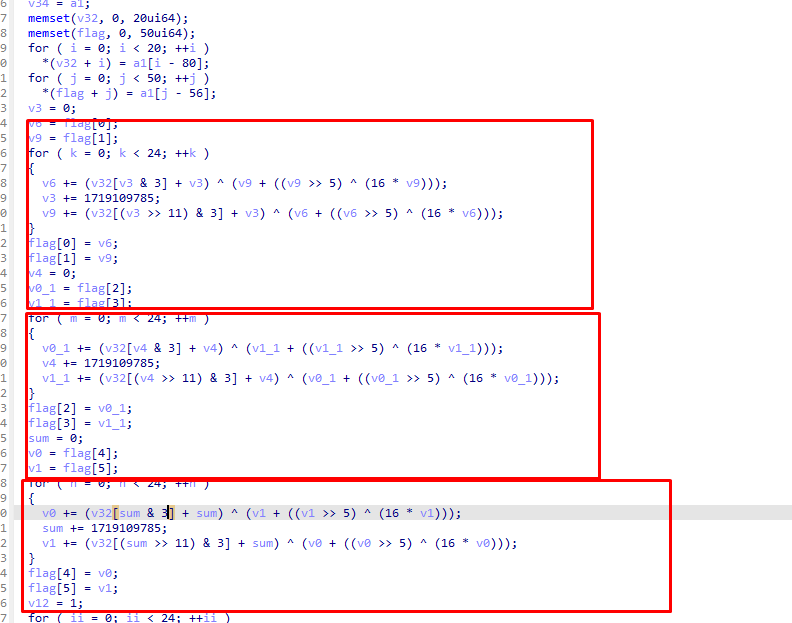
密文就是之前奇怪的函数里的值0xA6975621, 0xDEC4D51A, 0x4D829CA4, 0x56C845D1, 0x5C96B4A7, 0x2087494D
key就是最开始z3求出来的key 直接对着写脚本即可
1 | #include <stdio.h> |
LockedSecret
首先查壳 修改一下特征值 即可upx -d脱掉
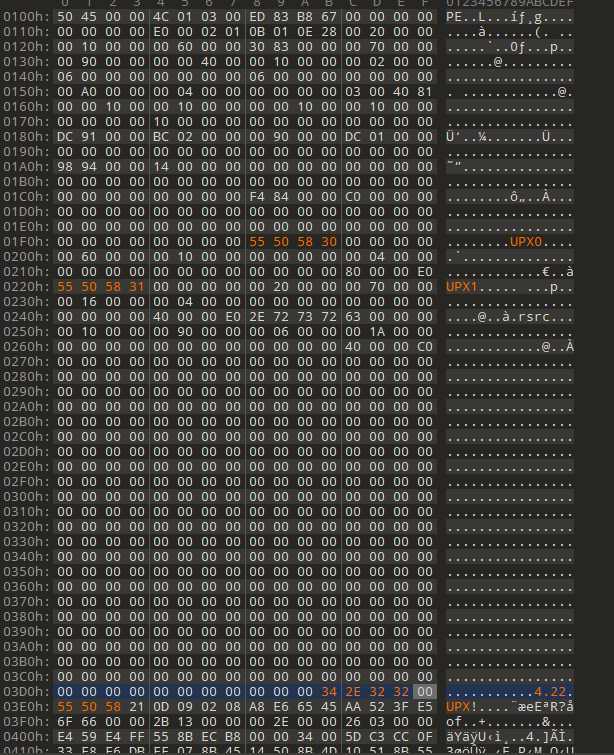
ida打开 逻辑很清晰 flag长度32
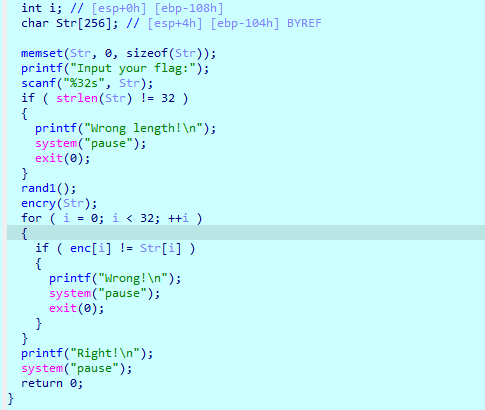
跟进encry函数 进行了很多自定义的加密 带有混淆 很难看
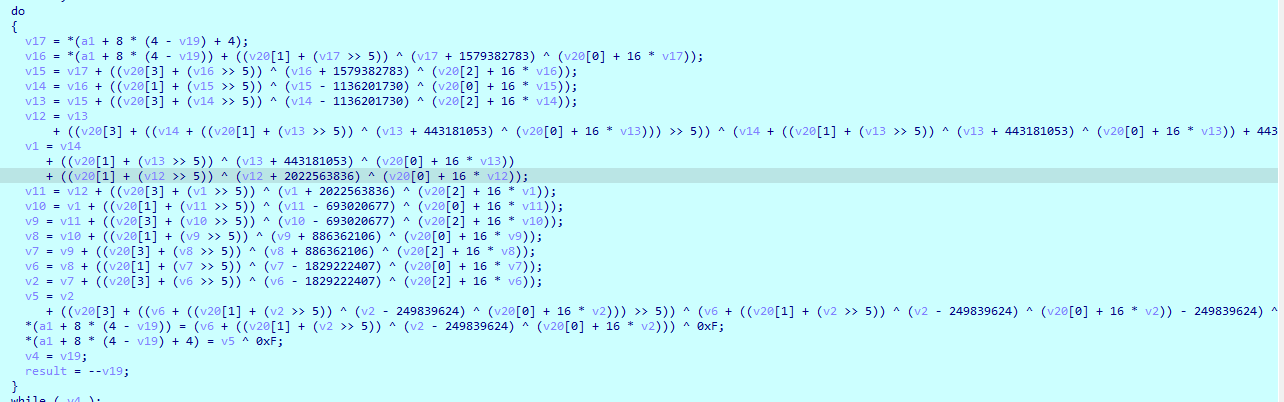
随后一点一点分析下面的逻辑 类似于tea加密 扔给deepseek 简化一下
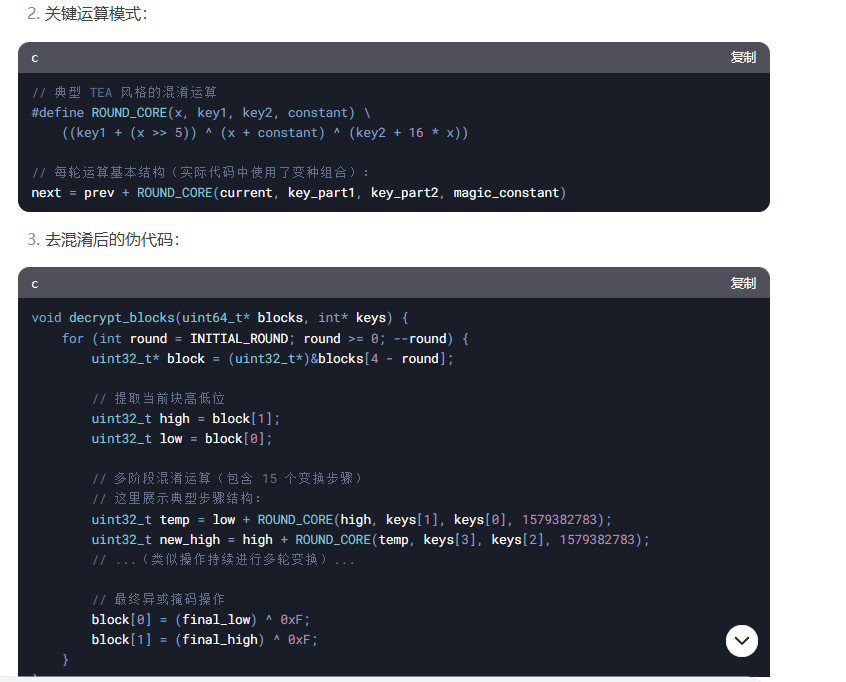
把这些看成一个整体 分为flag1和2
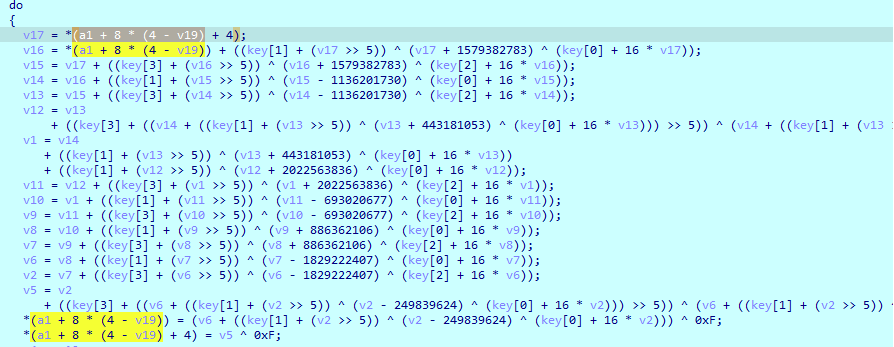
随后对照着加密 写出解密脚本即可 需要注意这个地方多处理一下即可
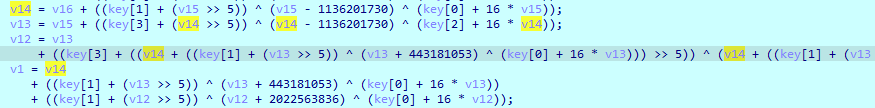
1 | #include <stdio.h> |
Mio?Ryo?Soyo?
python的exe 使用pyinstxtractor解包 注意版本是3.8
随后找个在线网站反编译 看反编译出来的代码 变量名很长 先修改一下
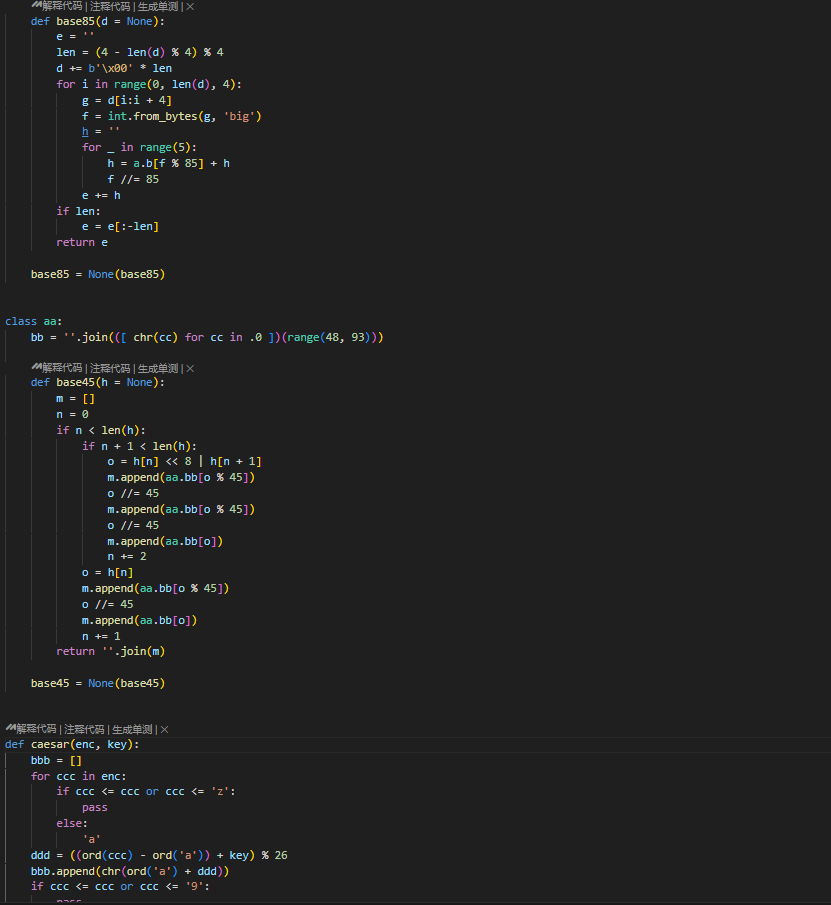
主要就是标准的base85 修改了码表的base45 还有凯撒
随后看密文以及加密过程
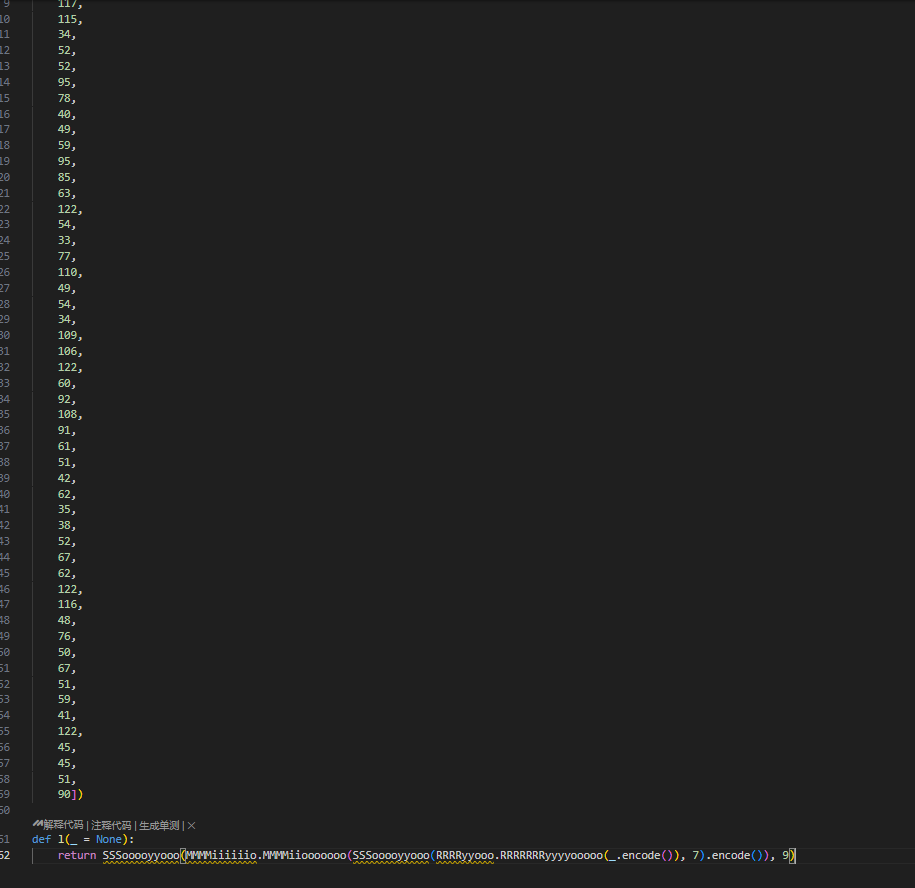
加密是base45-凯撒移位7-base85-凯撒移位9
直接写逆向脚本即可
1 | def caesar(enc, key): |
TimeSpaceRescue
根据题目描述 猜测需要时间戳爆破 范围是整个2024年
ida打开附件 有反调试 nop掉即可
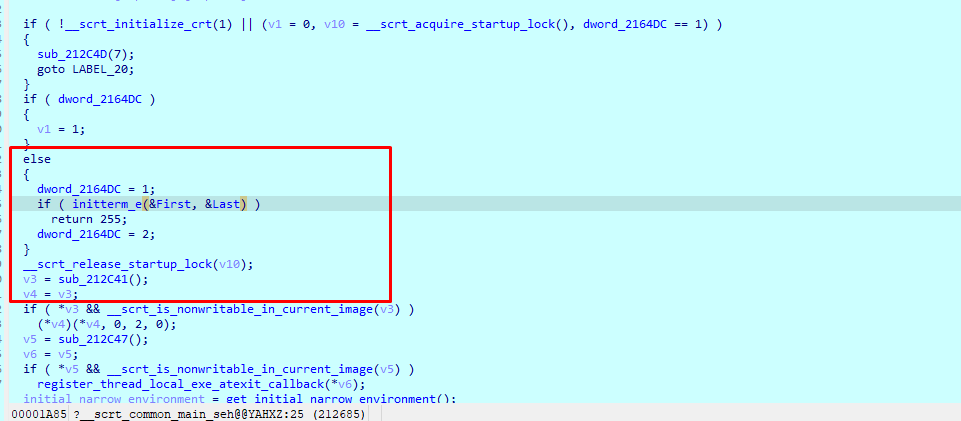
进入主函数 逻辑很清晰
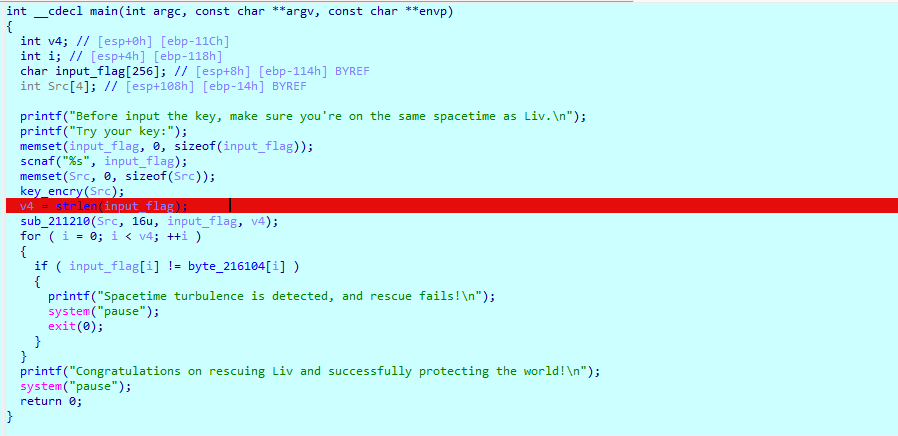
输入flag 根据当前时间的年月日 md5之后生成key 再根据key解密魔改的AES
跟进key_encry函数 有花 nop掉
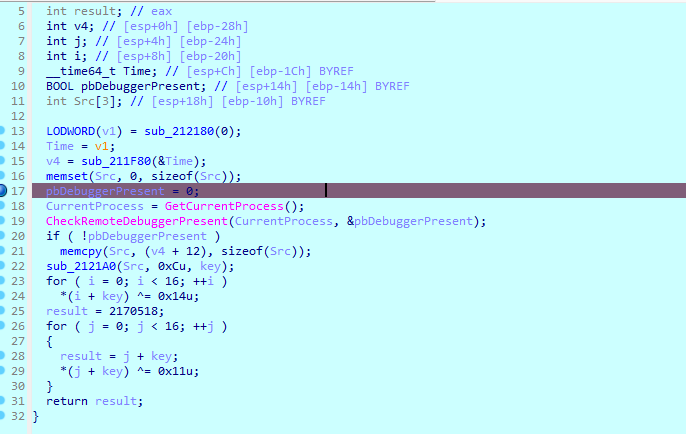
随后看sub_211210函数 找到魔改点
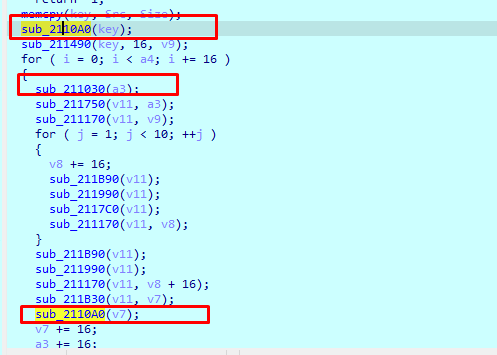
10A0就是xor 0x5然后交换位置 1030就是xor 0xf然后交换位置 直接根据这些约束 写脚本爆破即可 爆破思路是 先爆破前16位 如果有NSSCTF字样则是正确的key 再根据这个key解密剩下的密文
1 | import hashlib |
Room 0
ida打开附件 有花 先去掉
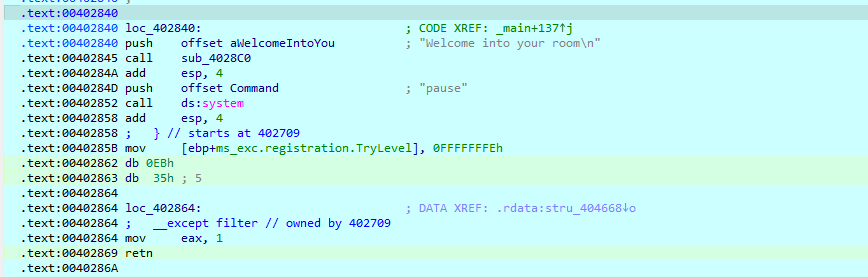
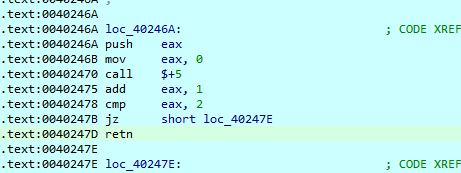
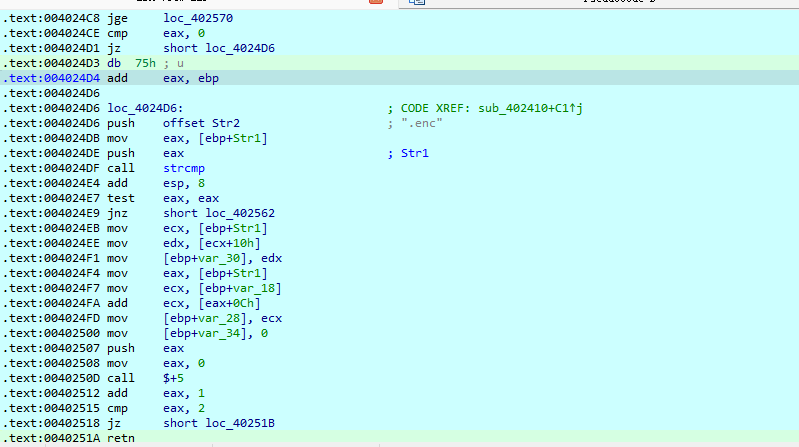
retn jzjnz花 直接nop掉 随后看主函数 逻辑很清晰
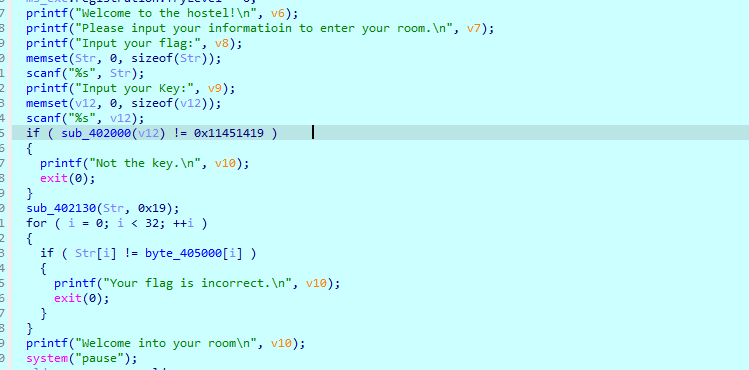
首先计算key key需要爆破 运算后的smc是一个函数 开头就是 push ebp mov ebp esp
所以前三位固定 爆破第四位 后来根据hint 触发除数为零的异常去爆破
1 | #include <stdio.h> |
得到key之后 打个断点 触发异常跳到smc段 也是retn jzjnz花 去掉即可
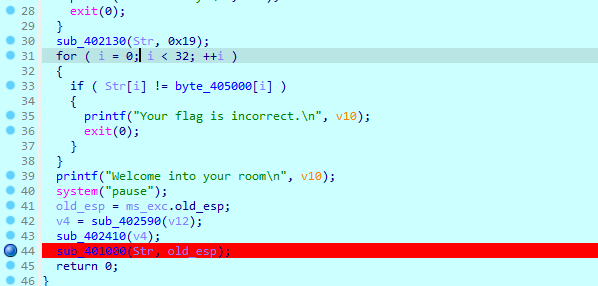
得到这么一个函数
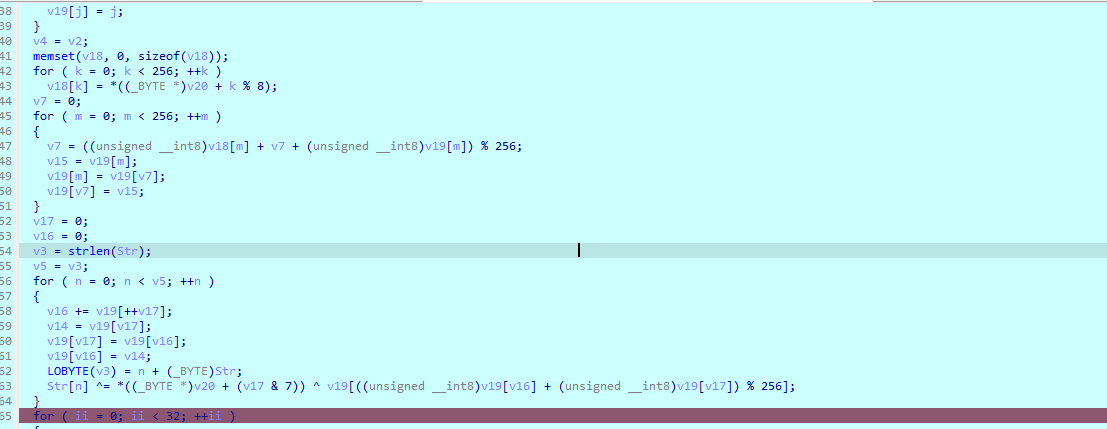
像是个魔改的rc4 最后的加密就是个异或 所以提取一下输入的密文加密后的值 得到密钥流异或密文即可
1 | print("A" * 32) |
Canon
ida打开附件 逻辑很清晰 直接起调试dump下来加密的各个case 没用到case2 7 所以不用分析
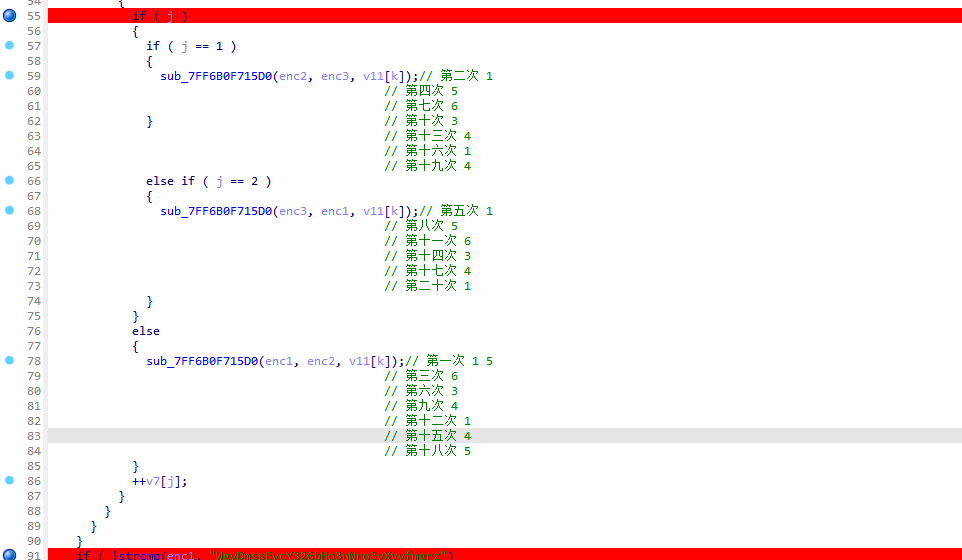
注意加密的base64是换表的
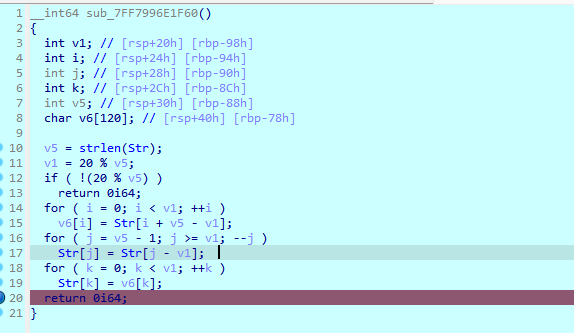
起调试dump下来
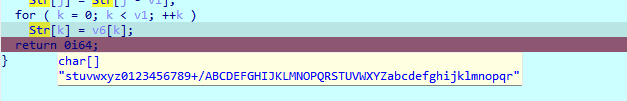
stuvwxyz0123456789+/ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqr
逆回去写解密即可
1 | import base64 |
腐蚀
ida打开附件 查看字符串 发现input.png 所以可以知道 是对enc进行了一些操作 得到png文件 根据字符串定位到函数
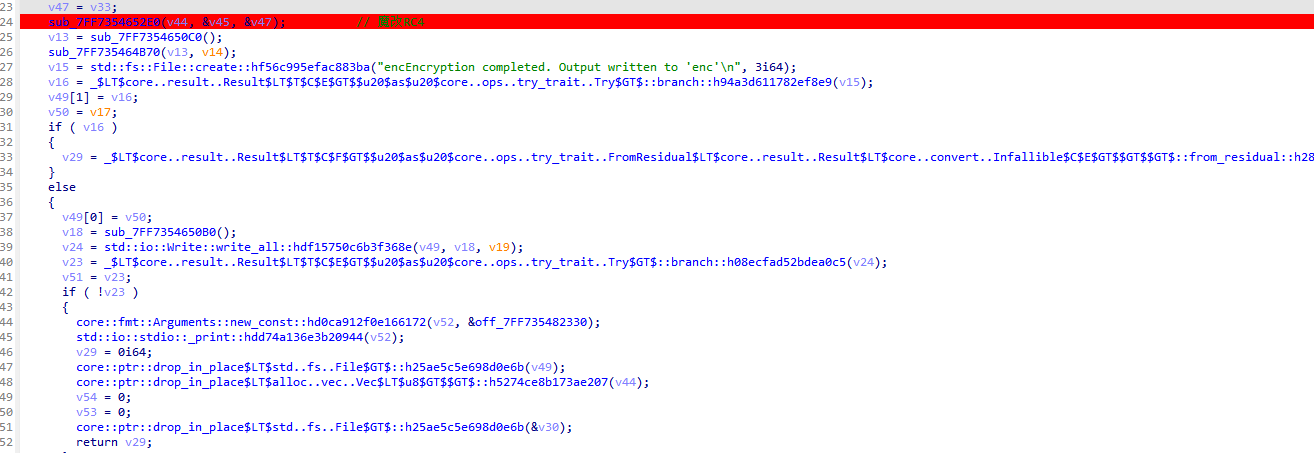
跟进sub_7FF7354652E0函数 发现256 最后还有xor 猜测是魔改的rc4 多xor了个0x1f
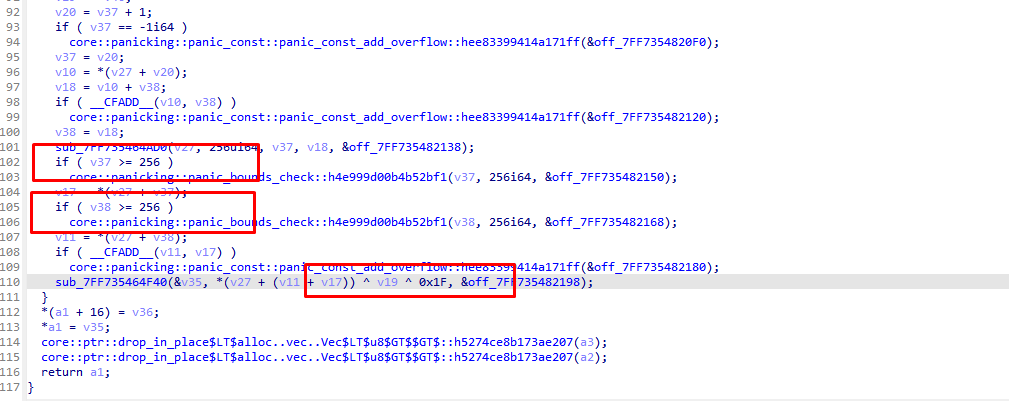
起个调试取出key0x60, 0x82, 0xAE, 0x42, 0x4E, 0x44, 0x49, 0x45, 0x1A, 0x0A, 0x0D, 0x0A, 0x4E, 0x47, 0x89, 0x50
随后在内存中看见 对输入进行了倒叙操作 所以加密流程就是 rc4 倒叙 写逆向脚本即可
1 | def rc4_decrypt(data, key): |
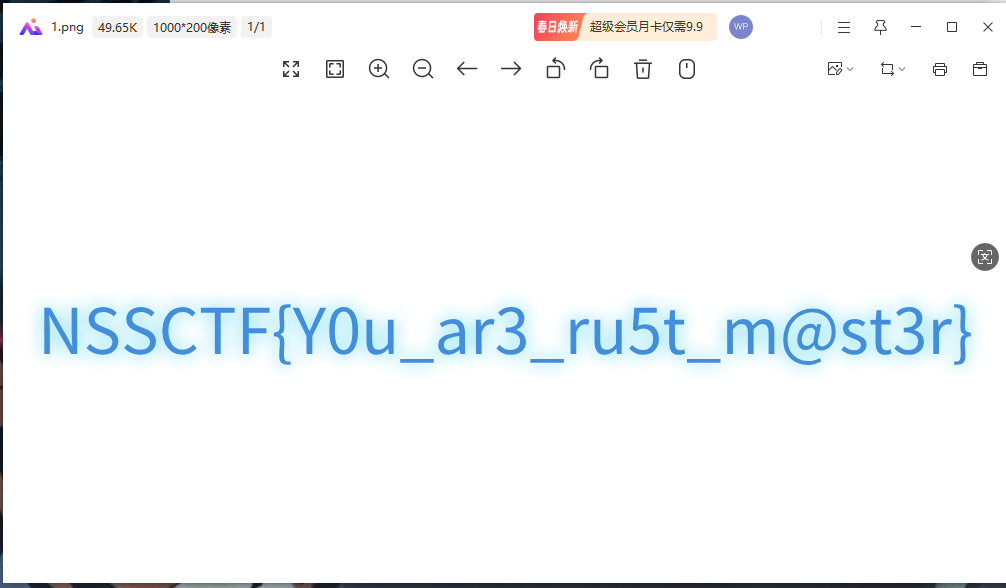
打开图片得到flag