2024 春秋杯夏季赛 RE wp
前言:这两天做了一下去年春秋杯夏季赛的RE 难度不是很大 知识面涉及的很广 希望今年的冬季赛也可以多做出来几个题
snake
python的exe程序 环境python3.8解包即可 把snake.pyc扔在线反编译里看一下 发现是一个RC4加密 最后异或的地方加了个跟循环次数的异或
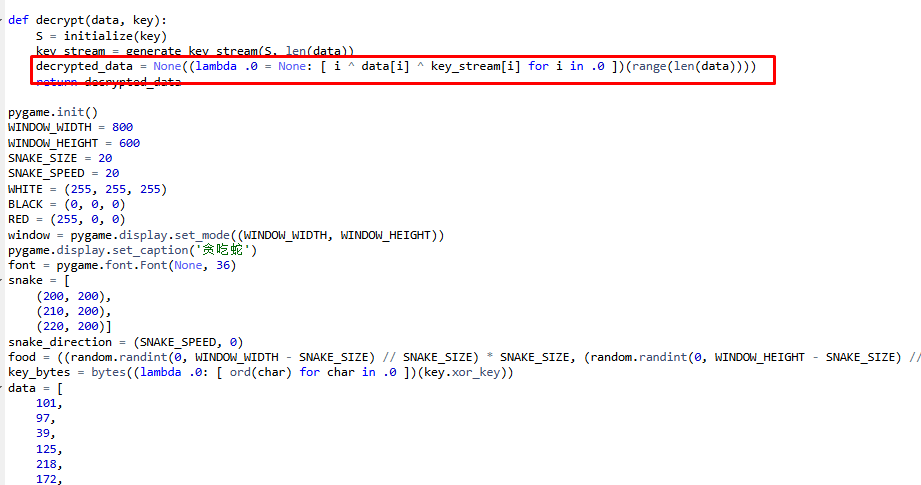
密文已知 在反编译一下key.pyc 找到密钥V3rY_v3Ry_Ez 直接写脚本解密即可
1 | def KSA(key): |
得到flag
HardSignin
打开附件 发现修改了UPX的特征码 010打开修改回去然后脱壳
ida打开附件 main的函数看不出来什么逻辑
发现TLS函数 跟进交叉引用一下
发现花指令 去除
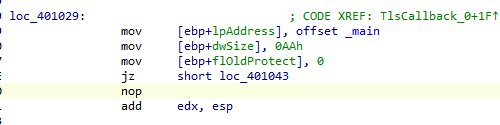
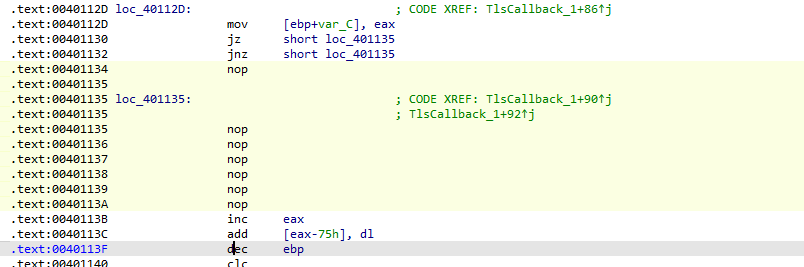
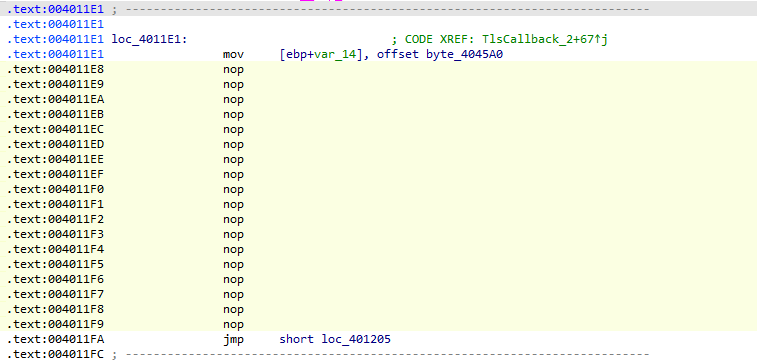
随后分析一下逻辑
TLS0是个smc 把main函数跟0x66异或 设置第一个随机数种子 用于TLS1生成变换的码表
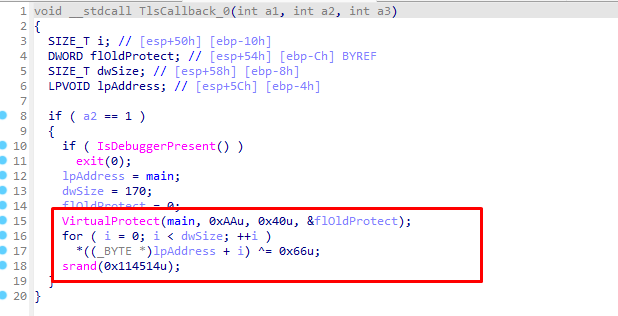
写个脚本解密一下
1 | lpAddress = 0x00401890 |
成功恢复main函数
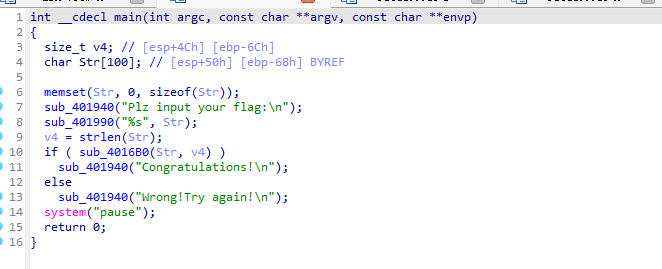
随后看TLS1
进行了一个码表的变换 设置第二个随机数种子 用于TLS2生成rc4的key和xtea的key
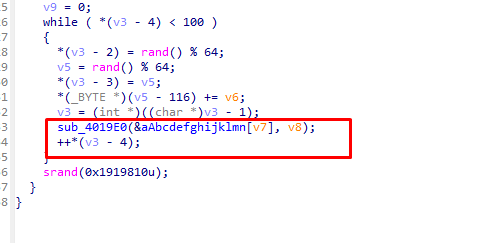
TLS2是进行了两个数的生成 交叉引用可以知道分别是rc4的key和xtea的key
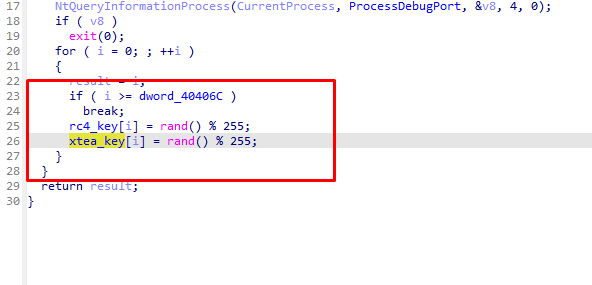
这几个函数都有反调试 直接patch即可
然后看主函数 逻辑很清晰 对密文进行base64换表编码 随后RC4加密 最后xtea加密
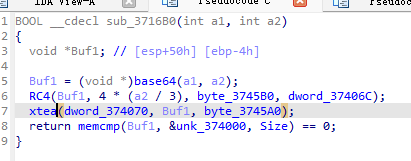
xtea魔改了一下 轮数是100

密文就是下面比对的unk_374000
我这里不知道为什么调试总是起不来 猜测可能是因为smc我手动解密之后 他TLS0重新跑了一次 把main函数异或回去了 所以索性静态写个脚本 跑一下key和变换后的base码表
1 | #include <stdio.h> |
得到rc4_key和xtea_key的key后 已知密文 直接写脚本解密即可
先解xtea
1 | #include <stdio.h> |
得到RC4的密文
0xbc 0xed 0x0 0x7b 0x86 0xf4 0x16 0x93 0x95 0xf9 0x87 0xdc 0x67 0xa8 0xa2 0x7f 0x4d 0xe2 0x62 0x9f 0x7b 0x34 0xae 0xe9 0x45 0x3 0x7e 0x35 0x42 0xd0 0x8b 0x70 0xf0 0xfb 0x2e 0xc7 0xdd 0xe9 0xb9 0x73 0xe3 0xcc 0x1a 0x75 0xad 0xdc 0xfd 0x14 0xa8 0xc8 0x45 0x16 0x31 0x6e 0x2a 0x8 0x2c 0xf 0x1d 0x9f 0x7 0xba 0xd5 0xef
随后解密RC4 + 换表base64
1 | import base64 |
得到flag
bedtea
ida打开附件 进入main函数
前面是两个反调试 还有输入的部分
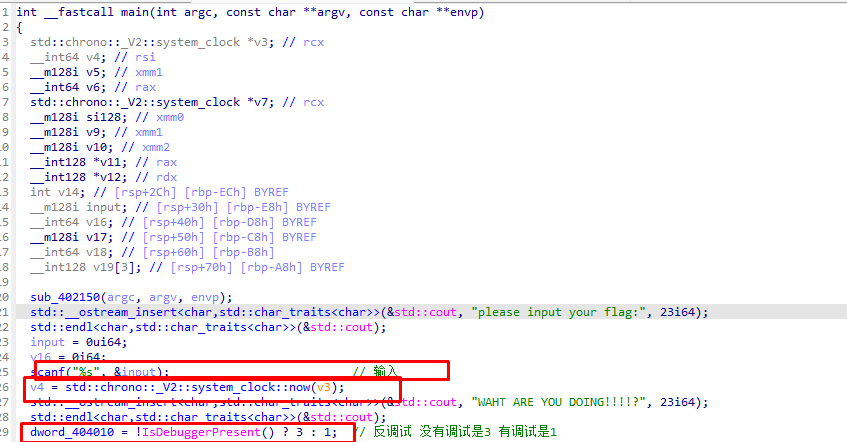
看下面的那个反调试 如果检测到调试是1 没检测到调试是3
随后往下看 发现有三个魔改的tea 修改了轮数 delta还有移位等常量值
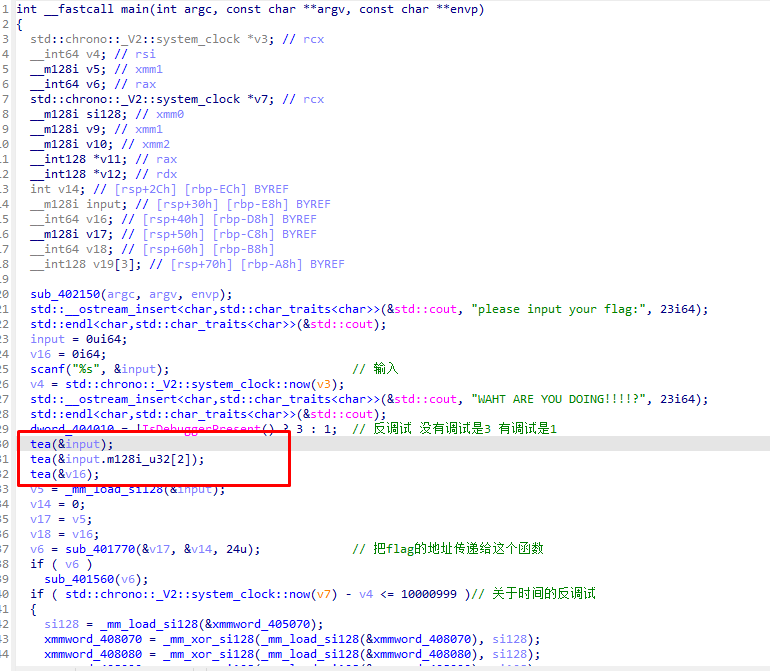
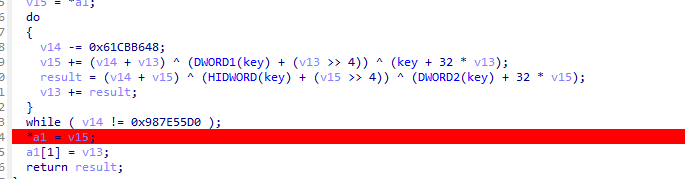
上面有个斐波那契数列计算tea的key
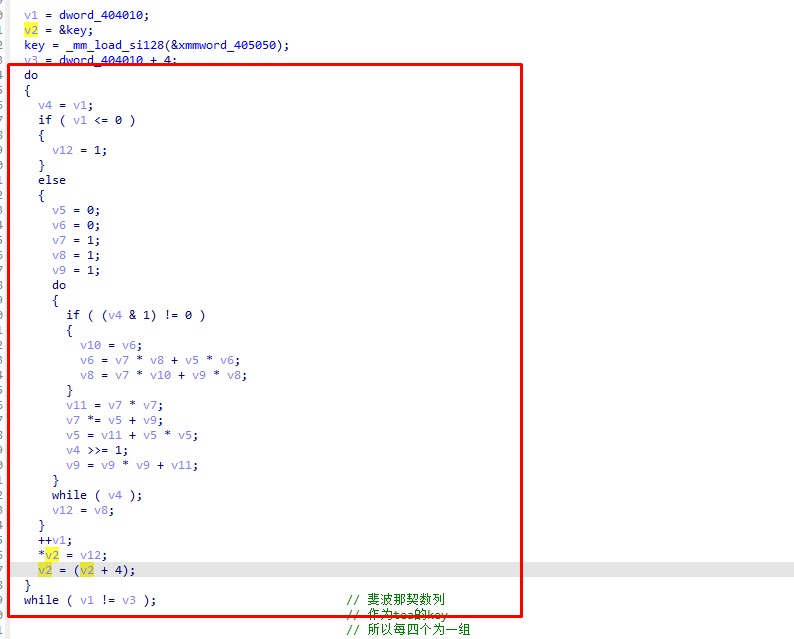
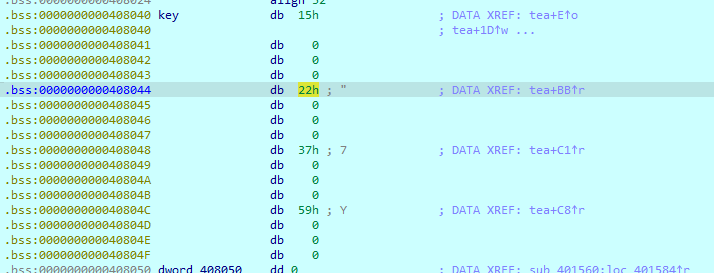
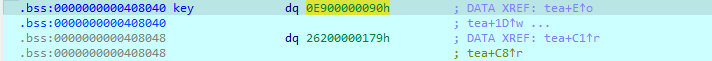
起个调试取出三个key 注意把第一个调试的值改为3才会生成正确的key
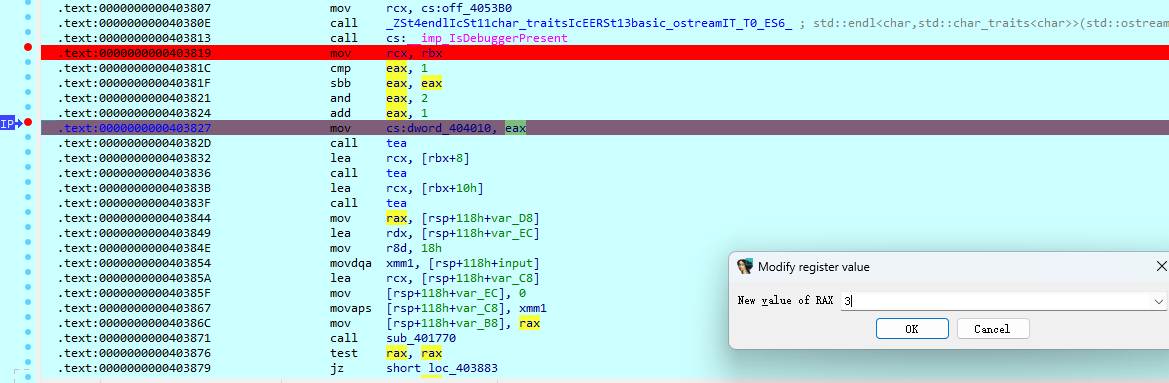
第一组key:3,5,8,13
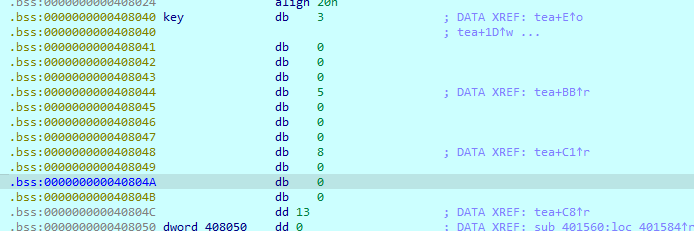
第二组key:0x15,0x22,0x37,0x59
第三组key:0x90,0xE9,0x179,0x262
随后通过二叉树对数据进行处理 这个地方的逻辑静态看有点费劲 直接动态对比数据即可
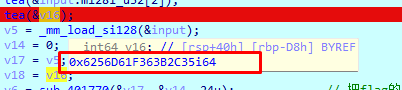

发现对数据进行倒叙处理
中间一堆看不懂的代码 经过动态调试 发现是跟0x33异或
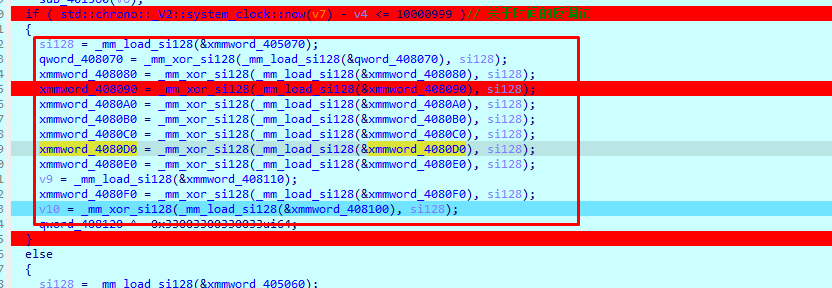
这里过一个时间的反调试 通过汇编可以看出函数在这个地方会进行跳转
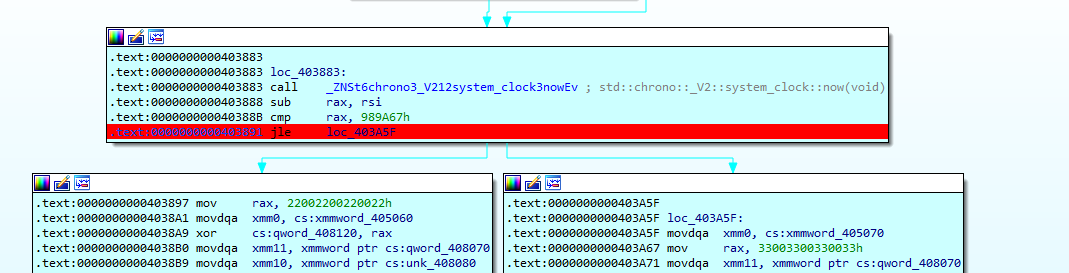
所以把zf值置为1即可过掉反调试
最后的地方存放三段密文
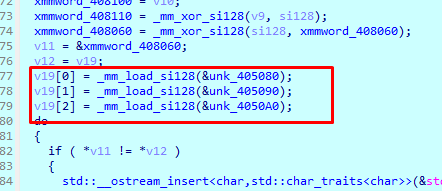
总的逻辑就是 先tea 然后倒置 最后异或0x33
直接写逆向脚本解密即可
1 | #include <stdio.h> |
得到flag