2024 ciscn&ccb RE wp
dump
运行程序 输入几个字符 观察回显
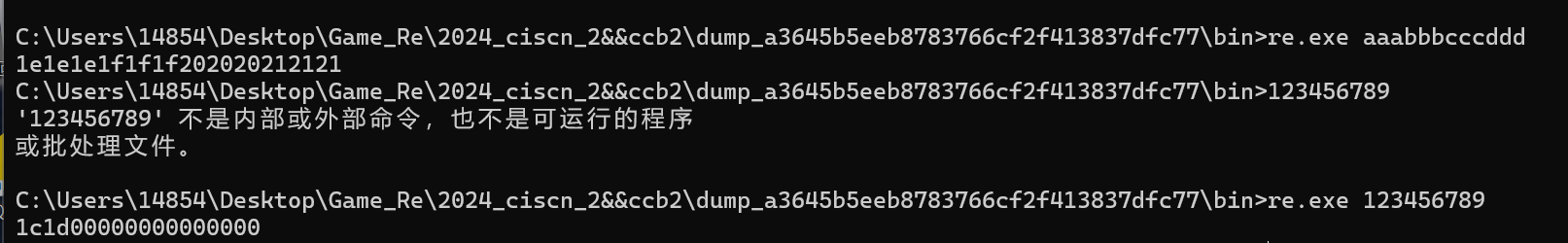
随后看了一下flag头的映射
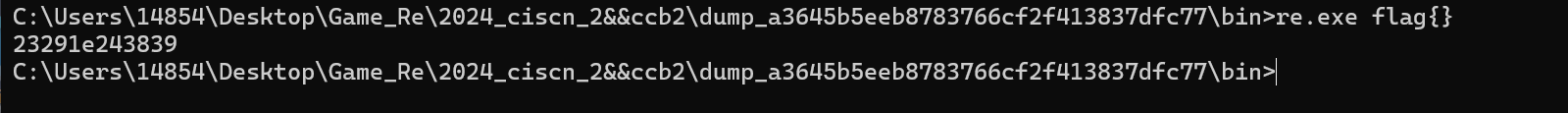
跟flag的前几位一样
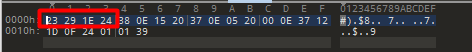
发现是单字节加密 所以将所有的可打印字符输入进去dump一下
1 | import string |
得到映射表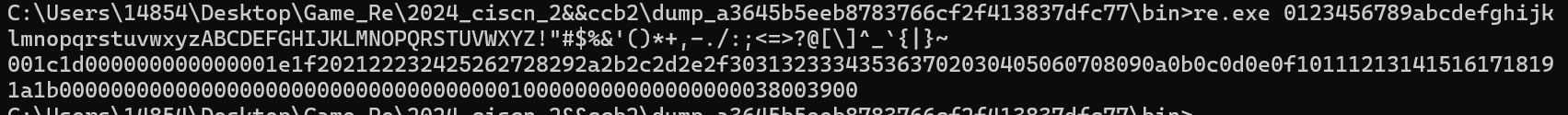
001c1d000000000000001e1f202122232425262728292a2b2c2d2e2f303132333435363702030405060708090a0b0c0d0e0f101112131415161718191a1b00000000000000000000000000000000000100000000000000000038003900
随后将flag一一映射过去即可
1 | import string |
手动修改一下flag 结合提示第十四位是4 直接改一下即可
flag{MTczMDc4MzQ2Ng==}
ezCsky
ida打开附件 得选择arm去分析 这里走了好多弯
发现有RC4 猜测rc4加密 找key和密文
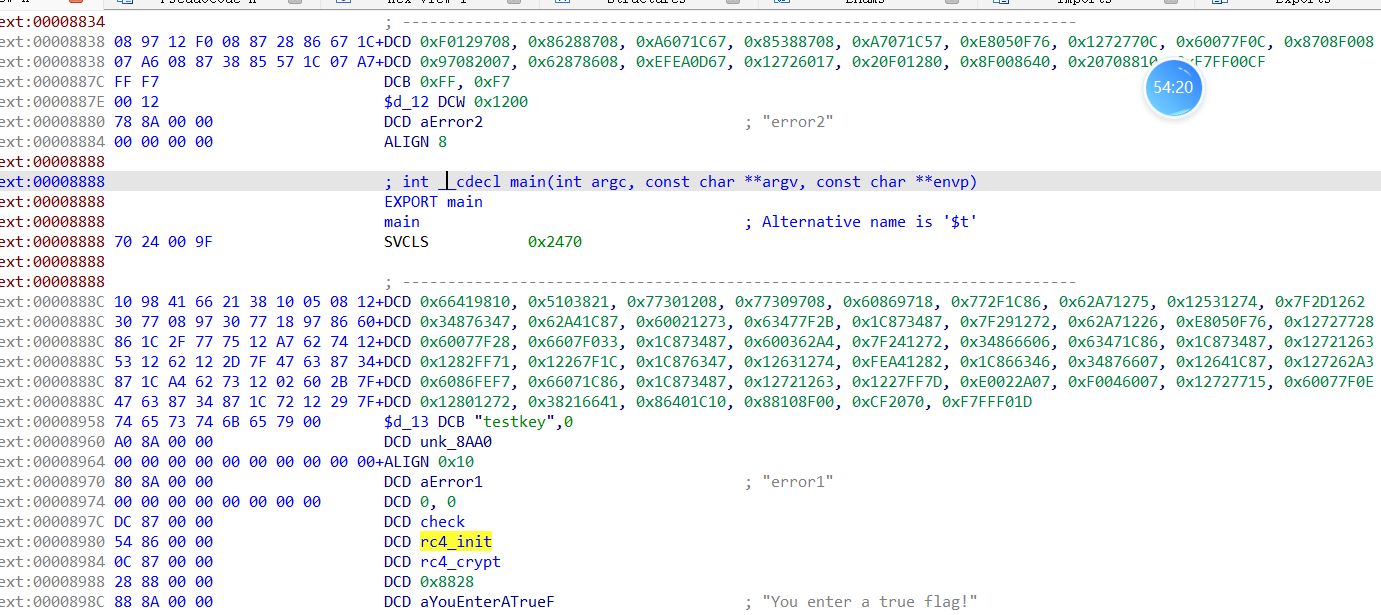
找到key 跟进unk_8AA0
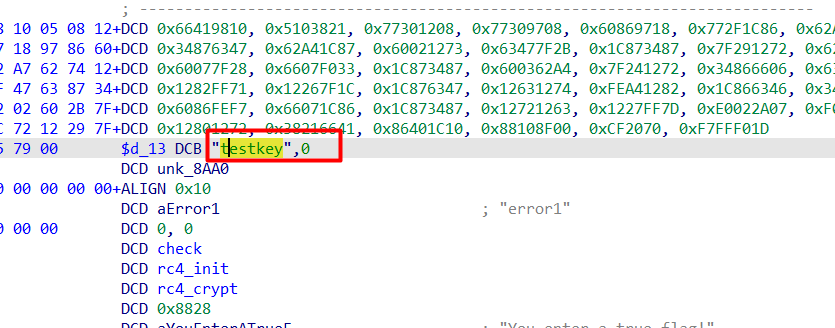
找到密文
直接解
1 | from Crypto.Cipher import ARC4 |
最后一位是} 前面的都不对 结合左边的符号表有xor函数
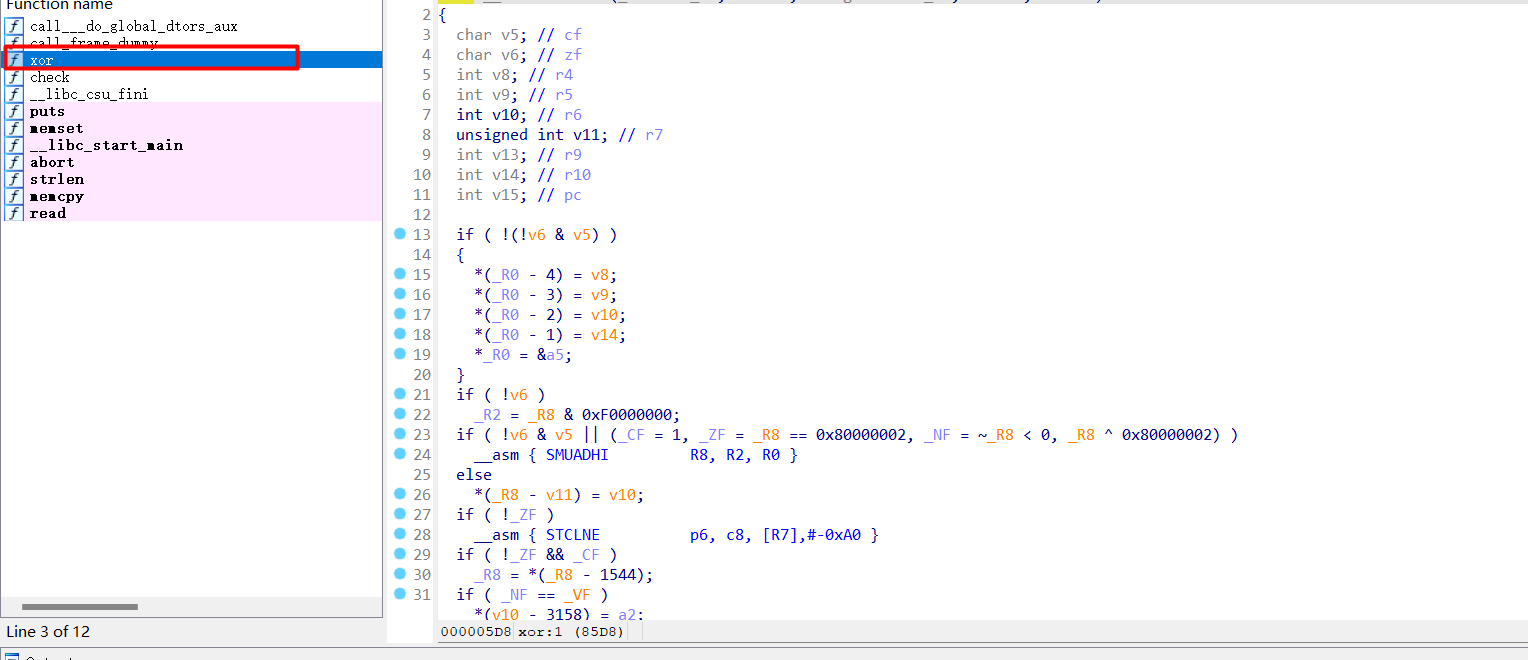
猜测进行了异或 但是最后一位没有异或 所以猜测加密的异或可能是
flag[i]^=flag[i+1]
直接写逆向脚本即可
1 | from Crypto.Cipher import ARC4 |
少了个f 在前面加上就是正确的flag
kiwi
打开附件 给了一个流量包和一个exe程序 分析一下exe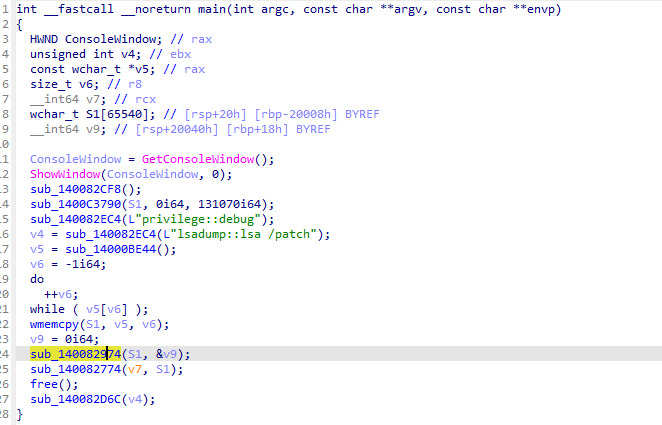
跟进一下sub_140082974
首先根据word_140111152生成了一个伪随机数 起调试取出来 是0x69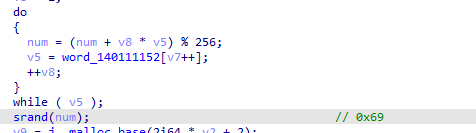
交叉引用这个伪随机数发现下面进行了异或 并且和随机数进行相加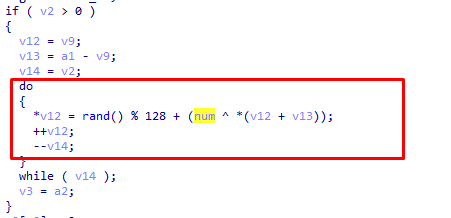
起调试取出随机数
1 | 0x7d, 0x2e, 0x10, 0x3d, 0x2d, 0x27, 0x44, 0x79, 0x27, 0x69, 0x33, 0x55, 0x5c, 0x2d, 0x7a, 0x4, 0x2, 0x65, 0x16, 0x22, 0x14, 0x2d, 0x4, 0x47, 0x1a, 0x7f, 0x26, 0x5b, 0x2a, 0x26, 0x69, 0x2c, 0x2f, 0x75, 0x25, 0x3d, 0x69, 0x38, 0x45, 0x62, 0x35, 0x6b, 0x27, 0x9, 0xf, 0x2a, 0x46, 0x5b, 0x55, 0x69, 0x16, 0x4, 0x4d, 0x65, 0x2f, 0x4e, 0x6a, 0x5a, 0x2e, 0x75, 0x4b, 0x77, 0x58, 0x37, 0x5, 0xf, 0x1, 0x2a, 0x22, 0x11, 0x2d, 0x52, 0x6a, 0x3a, 0x74, 0x73, 0x61, 0x9, 0x2b, 0x24, 0x10, 0x74, 0x40, 0x25, 0x8, 0x59, 0x66, 0x72, 0x25, 0x37, 0x72, 0x18, 0x10, 0x1e, 0x5, 0x48, 0x7, 0x64, 0x6c, 0x2a, 0x61, 0x1a, 0x44, 0x73, 0x4c, 0x3e, 0x62, 0x3a, 0x5a, 0x32, 0x72, 0x8, 0x3c, 0x6d, 0x5d, 0x2e, 0x4d, 0x71, 0x71, 0x5b, 0x52, 0x7d, 0x3c, 0x6d, 0x7f, 0x3, 0x38, 0x8, 0x3e, 0x5c, 0x2e, 0x65, 0x2d, 0x3b, 0x54, 0x6d, 0x65, 0x60, 0x38, 0x7, 0x2, 0xe, 0x62, 0x2e, 0x60, 0x3e, 0x35, 0x46, 0x22, 0x15, 0x17, 0x30, 0x79, 0x14, 0x52, 0x1c, 0x23, 0xf, 0x39, 0x1e, 0x31, 0x60, 0xe, 0x5, 0xe, 0x5c, 0x23, 0x68, 0x3d, 0x6, 0x40, 0x1, 0x62, 0x3, 0x45, 0x3e, 0x4, 0x4e, 0x10, 0x16 |
最后是一个变表的base64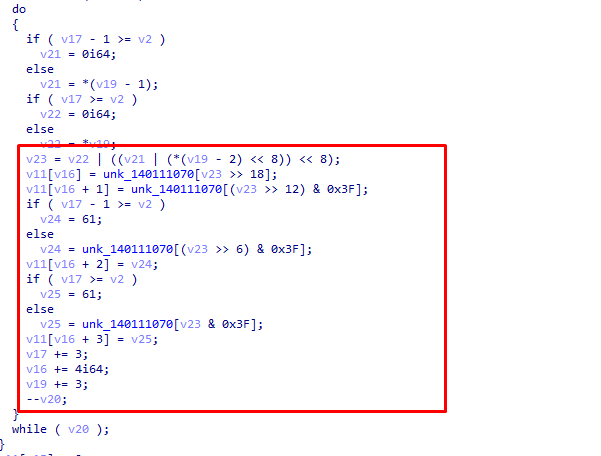
写个脚本提取一下码表
1 | import idaapi |
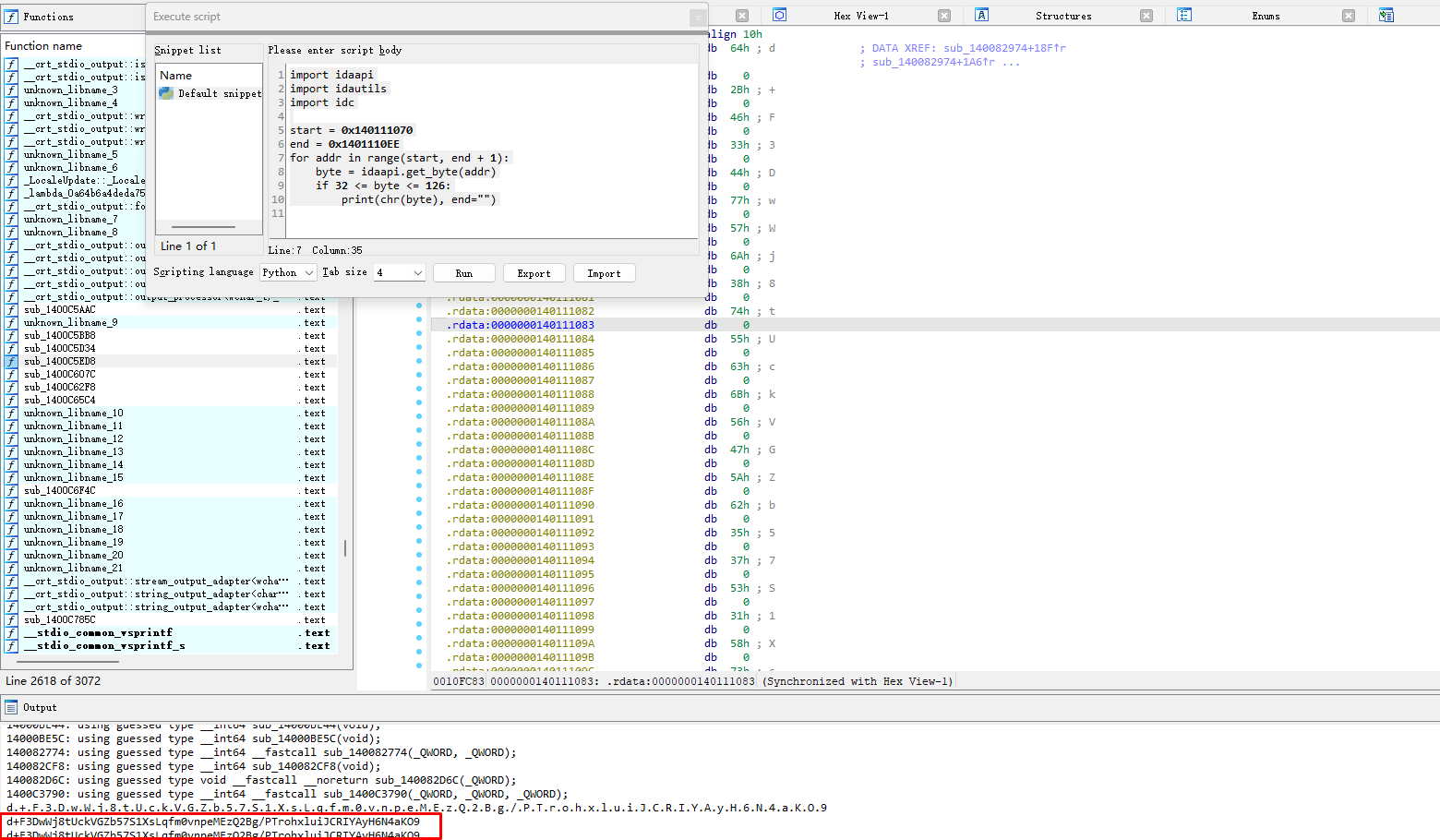
得到码表为d+F3DwWj8tUckVGZb57S1XsLqfm0vnpeMEzQ2Bg/PTrohxluiJCRIYAyH6N4aKO9
所以总的逻辑就是密文异或0x69加上随机数然后base64换表编码
随后看sub_140082774函数 发现密文是流量包的upload流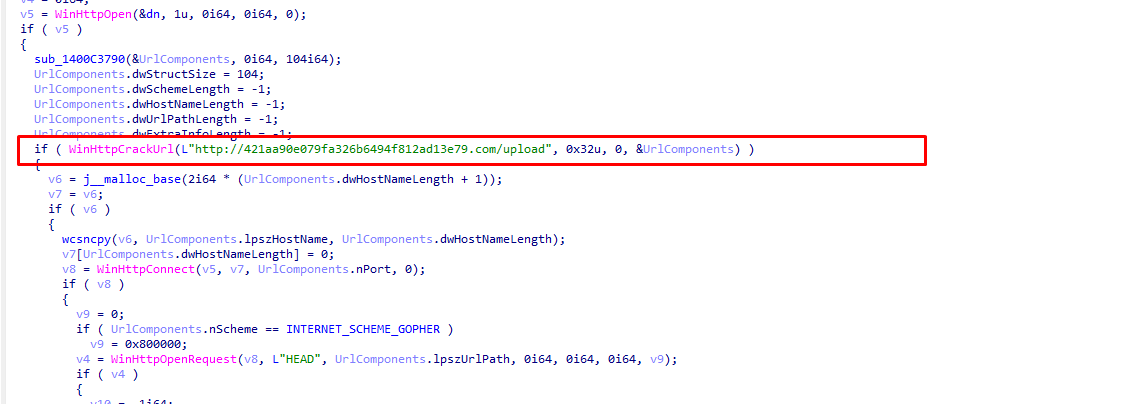
去流量包里找一下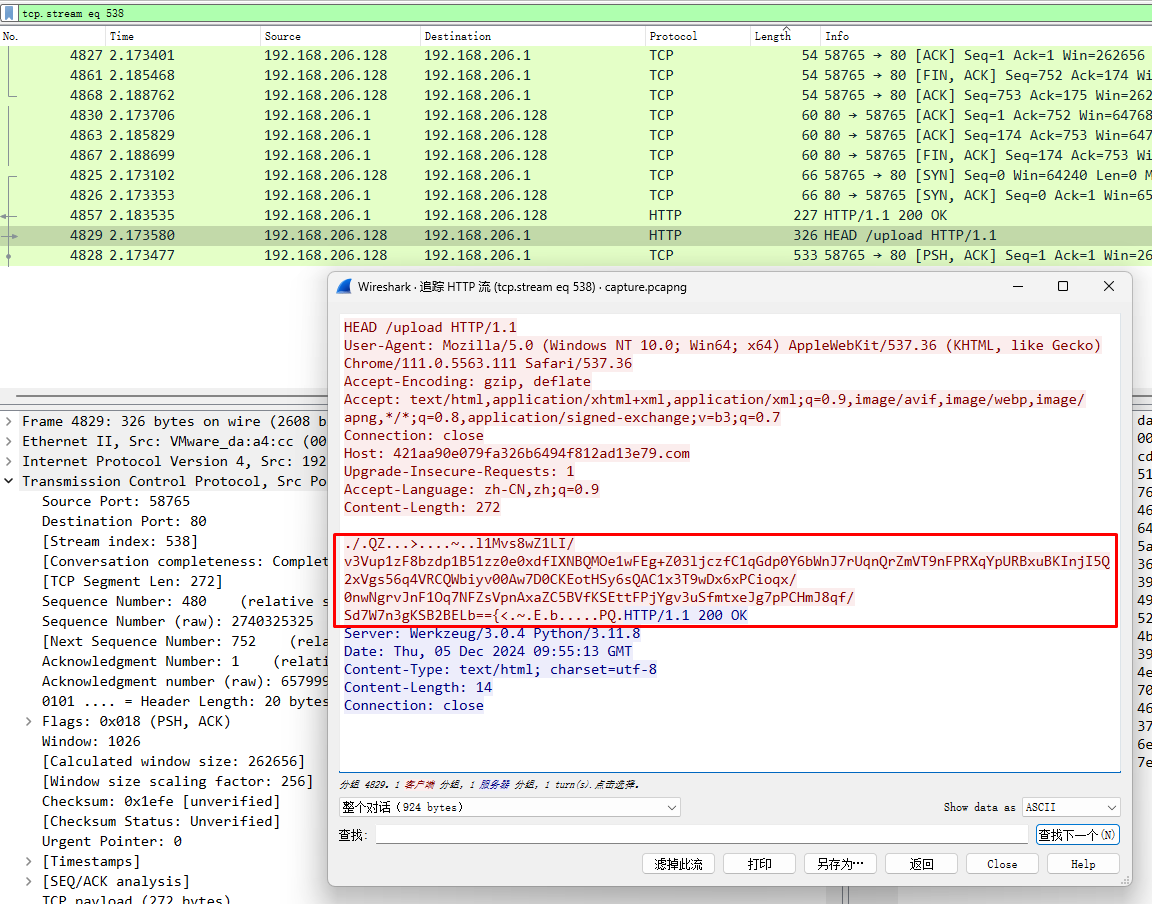
发现密文
先解码一下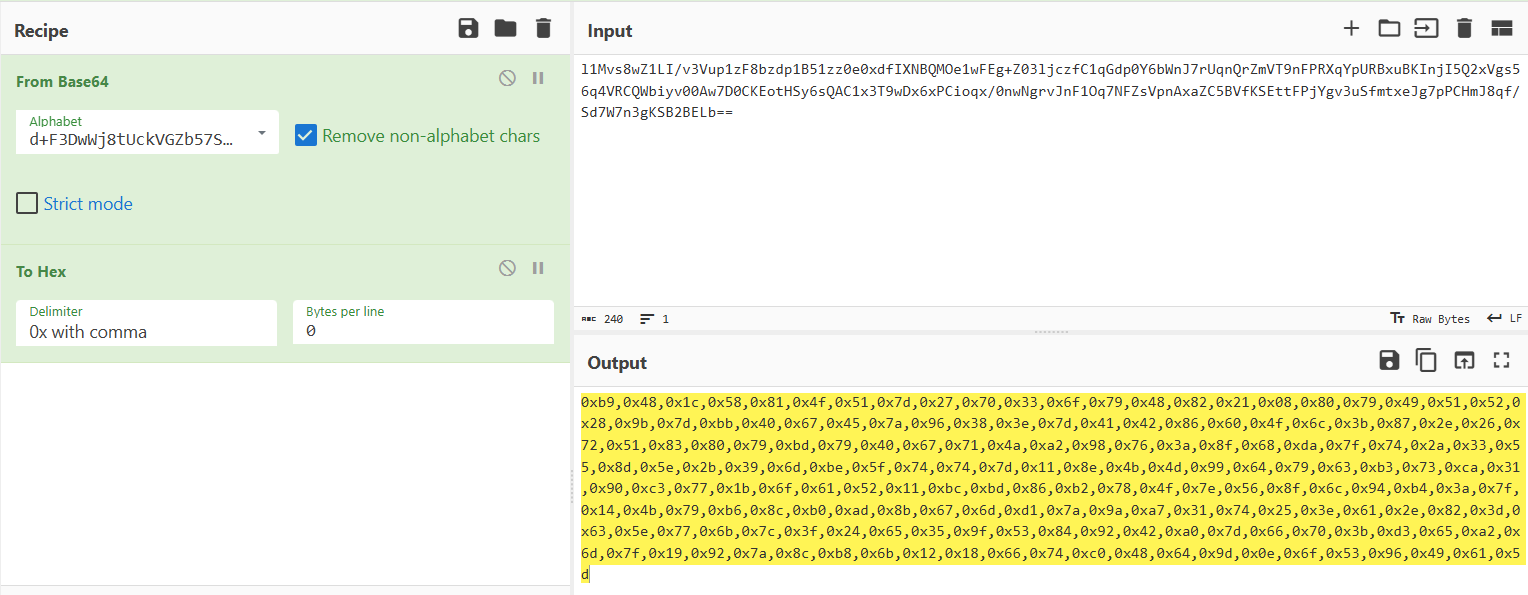
然后写个脚本解密
1 | enc = [0xb9, 0x48, 0x1c, 0x58, 0x81, 0x4f, 0x51, 0x7d, 0x27, 0x70, 0x33, 0x6f, 0x79, 0x48, 0x82, 0x21, |
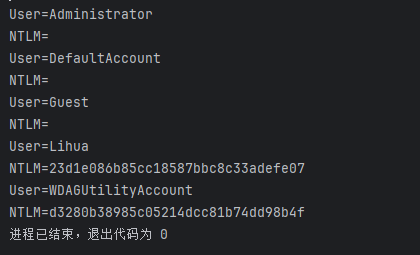
找个在线网站解一下Lihua的NTML即可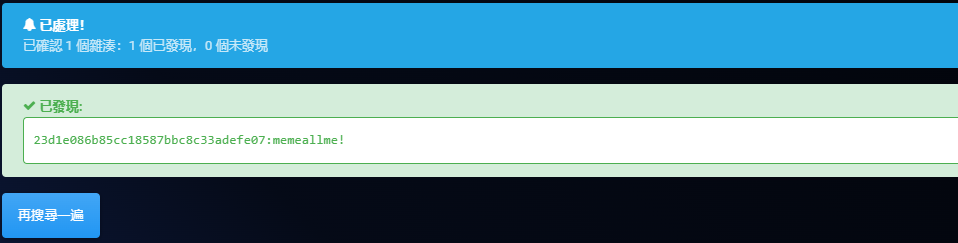
flag{memeallme!}